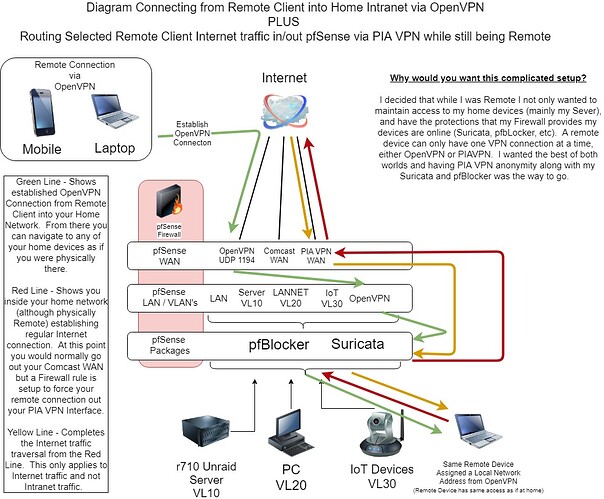
The setup for this is done in three parts and since there are many videos on two of the parts, I will simply include those videos.
Part 1: Setup PIA VPN on your pfSense. You have to have this completed and established before you can create firewall rules for routing your OpenVPN connections through this for Internet traffic. Please note, this is for PIA VPN and no others. You will have to do your own research on how to setup other VPNs with your pfSense.
Tom’s Video: https://www.youtube.com/watch?v=ov-xddVpxhc
PIA VPN Written Guide: PIA Support Portal
Part 2: Setup OpenVPN on your pfSense. Again, Tom has a great in-depth video showing how to accomplish this.
Tom’s Video: https://www.youtube.com/watch?v=7rQ-Tgt3L18
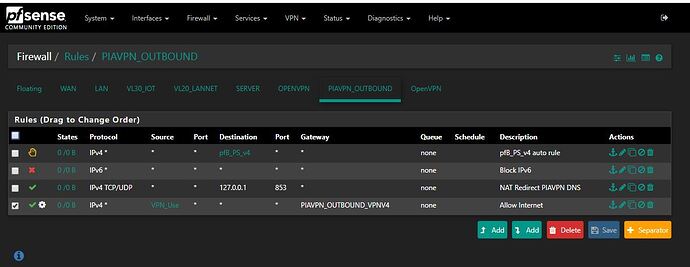
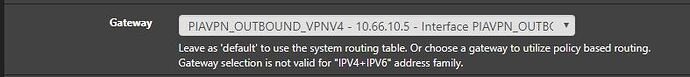
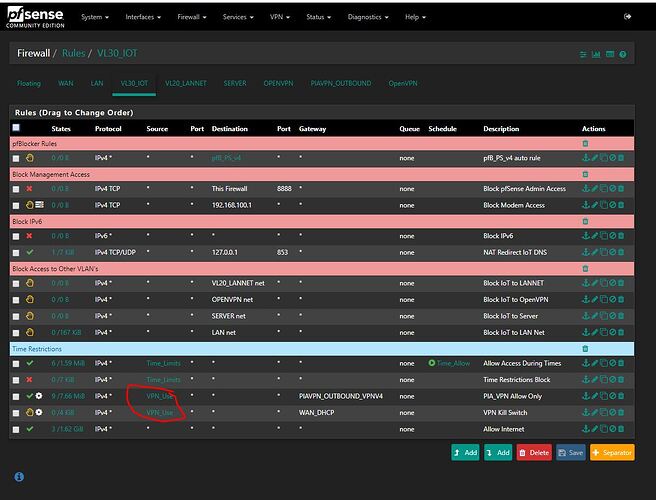
Part 3: This is where you create a firewall rule on your PIAVPN interface. Add the rule as shown in the Figure. You can ignore all the rules except the bottom one. IMPORTANT: Change the gateway to your PIAVPN Outbound one and not your WAN gateway. You can do this while creating the rule and the option is midway down the rule screen, see Figure.
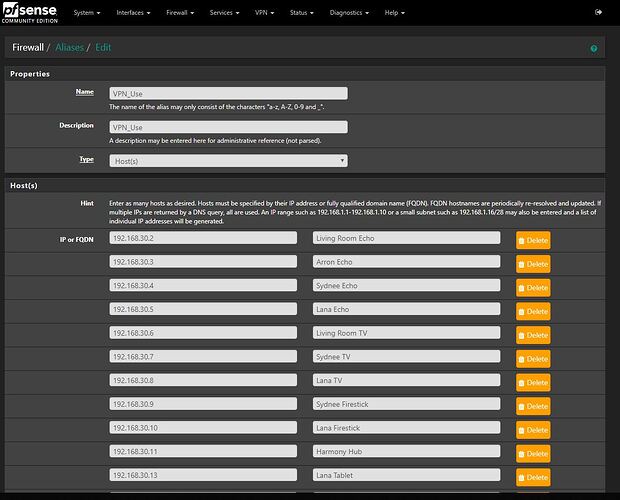
I statically map every device on my network. It makes making aliases very easy. You should do this for any device you plan on adding to this next step for creating an alias.
Create an Alias. I call mine VPN_Use, See Figure. Enter any device that you want to use the PIA VPN. This includes your OpenVPN connections. For example, if you get assigned a remote IP of 192.168.100.2 by your OpenVPN server, add that address to this alias.
Next, go into each firewall rule for each interface, including your OpenVPN Interface. If you don’t ever plan on using PIAVPN on a particular interface, then you don’t need this step. For me, I have various devices across my IoT, LANNET, OpenVPN, and Server (for virtual machines), that I want to use PIAVPN.
Rule order is important so make sure you get them correct by doing a lot of testing. Add the two rules circled in RED in the Figure FOR EACH Interface. Again, make sure you have PIAVPN for the Allow and the Kill Switch for WAN as block. You don’t need the kill switch but if you are worried about the devices on your Alias not using the VPN then you should keep this rule too.
I hope this help most people who are interested in this type of setup. I will try to answer questions as the come up but please make sure you follow the proper setup for getting both OpenVPN and PIAVPN working independently BEFORE doing this.