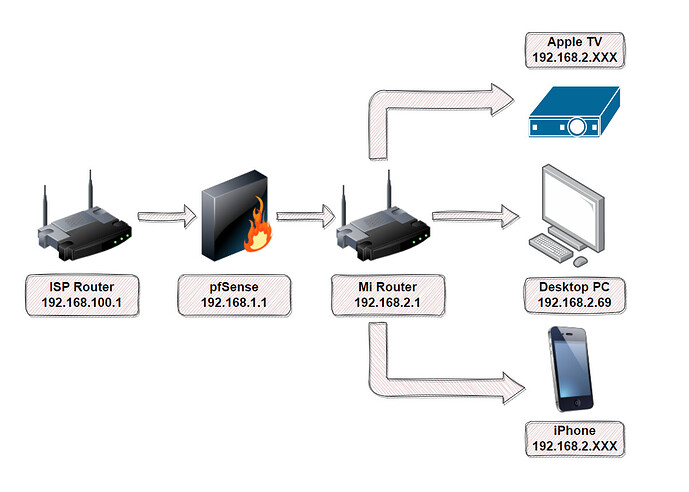
So, I’ve been having issues for a few days now with pfSense after installing it on t730 that I picked up just for this purpose. Here’s a diagram of my setup, just so we’re clear about how everything’s going.
So, as you can see. I’m feeding my ISP router directly into pfSense, which has (1) WAN and (1) LAN, and the LAN is feeding into Mi Router that I use to pass on internet via wireless and ethernet to several devices, such as my computer, phones, Apple TV, Smart TV, PS5, et al.
Now … I want VPN on router level for Apple TV, as there’s no other way to bypass regional restrictions to consume content on there. But I don’t want VPN on my personal devices at all times, I want to be able to pick and choose when to add and remove that. Ergo, I was hoping if I could create two aliases namely VPN and NoVPN, and throw in the IPs in their respective aliases for where I want to route my traffic through VPN or not.
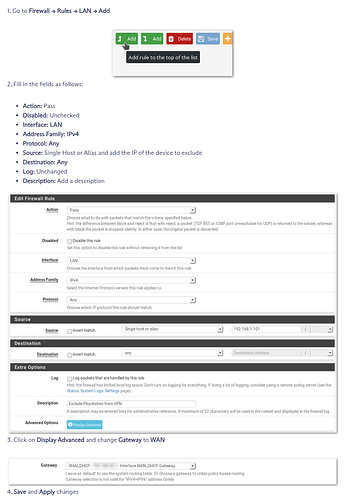
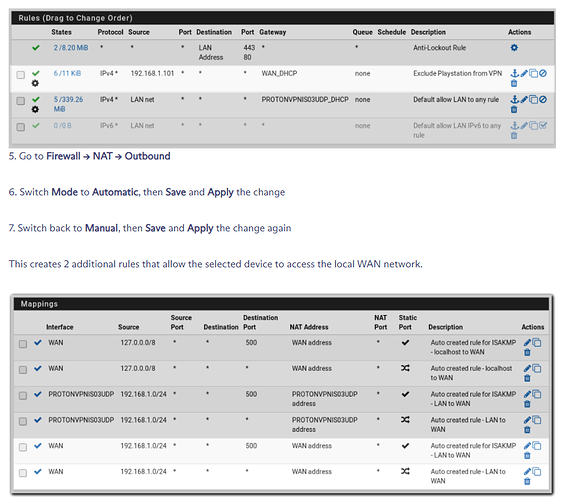
Now the problem is that, every tutorial I read online basically said add firewall rules for LAN in pfSense by simply doing the following:
Disclaimer: screenshots are taken from ProtonVPN’s pfSense 2.6.x guide lin.
When I follow this step, and put my desktop IP in there as 192.168.2.69, and make sure that on my computer I assign a static IP to correlate that, it doesn’t do anything. All of my traffic on computer still routes through VPN, I’ve been at it for the past couple of days or so and can’t figure out what I’m missing here.
Any other set of eyes and help on this would be greatly appreciated, if you need any more info on how the OpenVPN is set up or my gateways, let me know and I’ll share them accordingly. But I feel like the fact that I’m adding another router after pfSense which puts me on another subnet, maybe that’s why I’m having a hard time not being able to exclude my desktop from VPN traffic and maybe need to create something else in pfSense? Either way, let me know what you guys think.