Hello everybody,
First of all, I would like to apologize for the confusing topic, I had some troubles making it short and insightful…
On a certain LAN subnet that has several computers that I wish to access remotely, there is one computer running OpenVPN as a server (Tun, On Windows).
LAN subnet: 10.0.0.0 (Gateway-Router, separated from VPN is on 10.0.0.138).
VPN range: 10.8.0.0/24 (OpenVPN Server is on 10.8.0.1).
I have followed the “Extending the scope” part of OpenVPN’s How-to. I’m pushing “route 10.0.0.0 255.255.255.0” to the clients, IP forwarding is enabled on the VPN server windows machine and I’ve added a static route to my router. I’ve also disabled the firewall for the interface that Ovpn is using. I can access that VPN server, I can ping the gateway and in general, things seem to be working just fine.
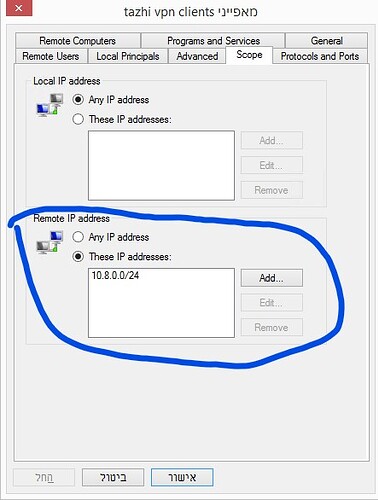
The problem applies to computers running Windows Firewall (I’m guessing it will happen with other firewalls too), for example, the one at 10.0.0.10, which I’m trying to access for RD and for file sharing. When the firewall on that computer is completely disabled (Which is not a good practice), I can access it through the VPN without any issues. However, when I enable the firewall, I lose the ability to reach it. I tried allowing incoming connections through specific ports (RD and SMB ports, for example) from the desired scope (10.8.0.1/24), which didn’t fix the issue. In addition, I also tried simply allowing all traffic from that scope to low, but that didn’t work either. The thing that confuses me the most, is that from my understanding, allowing all traffic from that scope to enter, which doesn’t work, is almost like turning off the firewall completely, which does work, so I just don’t get where the issue is at.
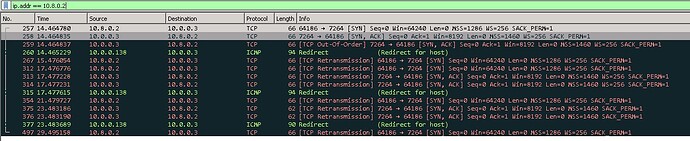
I have taken a look at Wireshark while the firewall was turned on, with the rule that allows all traffic from 10.8.0.0/24 to flow, and it does show incoming requests, but as far as I understand, they get rejected, redirected, etc. I will admit that I’m having some problems understanding everything that Wireshark throws at me (It’s a hobby…)
I’m also linking 2 screenshots of Wireshark ping updates (Sorry for the confusion, when I took those screenshots, my VPN range was changed to 10.8.0.0):
This one is running on the target of the ping, with its firewall enabled, with a general rule of allowing traffic from VPN subnet: https://imgur.com/RMRddko
This one is running on the computer running the VPN server: https://imgur.com/dlS6Tu9
I have a feeling it is a routing issue, but I just can’t figure out what or where.
OpenVPN Server config:
config
dev-node “Obelisk”
topology subnet
server 192.168.5.0 255.255.255.0
port 49361
proto udp4
dev tun
tls-server
tls-crypt “C:\Program Files\OpenVPN\config\ta.key” 0
ca …
cert …
key …
dh …
keepalive 10 120
cipher AES-256-GCM
auth SHA256
push “route 10.0.0.0 255.255.255.0”
persist-key
persist-tun
verb 3
I’m not a professional of any sort, but I am trying to learn and to do my googling for solutions before posting.
I’ll be more than happy to provide any more info necessary.
Thank you so much!
Noam.
 .
.