What really started to grind my gears was the rules. When I started to create a rule, I noticed I had a choice in “direction” which caught me off guard. Direction? Wasn’t this a stateful firewall? Ok, I thought maybe it was just a weird way of handling source / destination… Nope, they literally mean in/out of the LAN interface. I thought to myself, this doesn’t bode well.
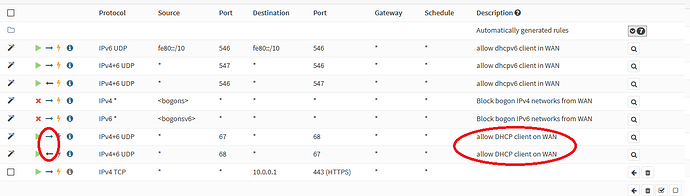
Then I looked at some automatically generated rules - which I’m happy they make apparent but not happy there’s no way to directly modify them. For the WAN interface, if you set it to DHCP it automatically creates an in/out rule for DHCP, to allow the WAN to get an IP… I honestly hate dealing with rules like this. Why do I need an inbound rule if the firewall is initiating the connection to get an IP address? So now I have this inbound rule open 24/7 exposing any vulnerabilities to the DHCP client daemon? wtf?
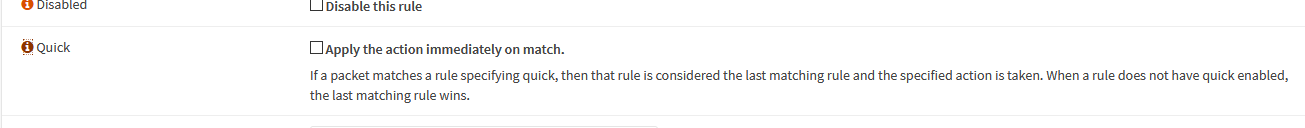
Ugh and this stupid feature… “quick” which ignores firewall order basically… By the way, it’s checked by default. I feel like this firewall is a paint by numbers version of pfsense.
so… use PFSense, or Untangle, or something else? Frankly if I were trying out OPNsense and saw this, I would stop using it. And I’ve never tried it before. So thanks for sharing this because now I never will.
2 Likes
Oh yea this is a deal breaker for me - I just thought I would give it a fair shake. I’m always up for trying new things out even ones I find hard to use at first. I honestly don’t like the GUI for opnsense, it’s form over function mostly.
I just wanted to share this, because it isn’t exactly apparent and being a fork of pfsense, it is unexpected.
**I started out with m0n0wall and have used pfsense since it released, so this was a trial run.
1 Like
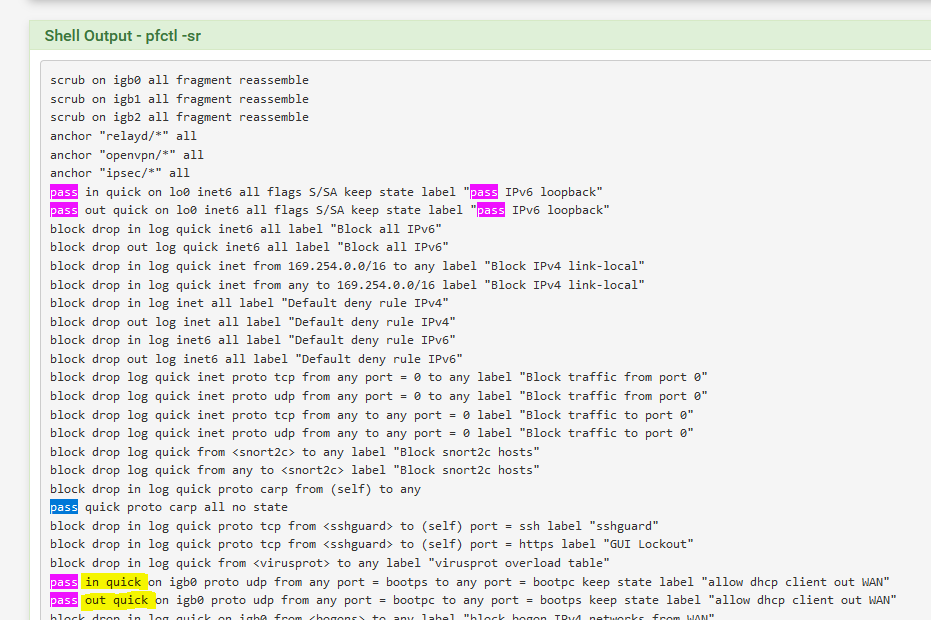
Hmm well apparently pfsense does this too, but you do not see the rules in the GUI. Little bit “TIL” I guess. Last two rows are pass rules on the WAN interface, both in/out.