Hello everyone,
I’m a sysadmin at a small business in Switzerland.
I’ve recently started to do some research about the possibility to filter our inter-VLAN traffic actually handled by our Cisco L3 switches.
It seems that the most efficient way to filter this traffic is to let a firewall do the routing as opposed to ACLs on Cisco that could quickly become a nightmare to manage.
We currently have a Forcepoint firewall that is owned by the ISP and that we manage internally. The ISP also handles our MPLS traffic between our headquarters and 3 other branches.
The Forcepoint firewall is expensive and cannot handle our LAN traffic and that’s why I decided to try Untangle that I installed on one of our old ESXi servers.
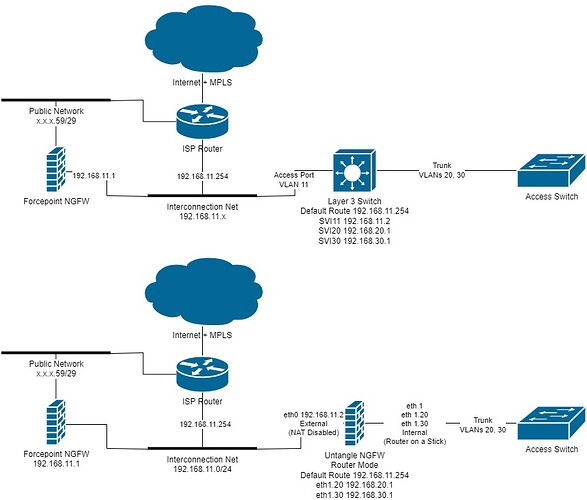
At the top, you will see our current network topology and below the way I would implement the firewall.
If everything goes as planned I would like to completely replace the Forcepoint firewall in the future and buy some Untangle licenses to unlock the more advanced filtering features.
What do you think about this configuration? Will everything work as expected?
I also have some doubts about the Untangle sub interfaces configuration. I already did some testing and it seems that the main interface traffic is untagged and only the sub interfaces generate 802.1q tagged traffic. That means on the Switch side I have to configure the trunk native VLAN to match the main interface configuration and the additional VLANs as “allowed vlans” on the trunk.
Would it be an issue if I just set the main interface IP to some bogus network I do not use and only use the sub interfaces to do the routing? I’m a Cisco guy and on routers I normally do not set any ip for the main interface, but it’s mandatory in Untangle.
Thanks a lot for your help and kudos for the great content and community.