I could use some ideas/suggestions with the last stage of my new network setup.
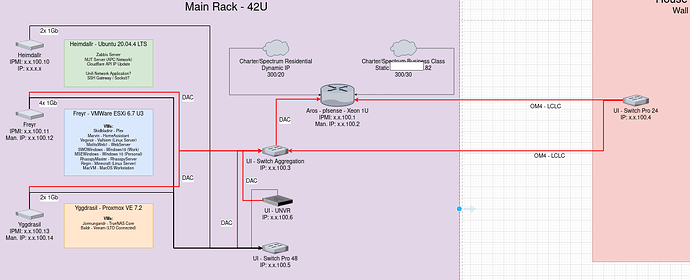
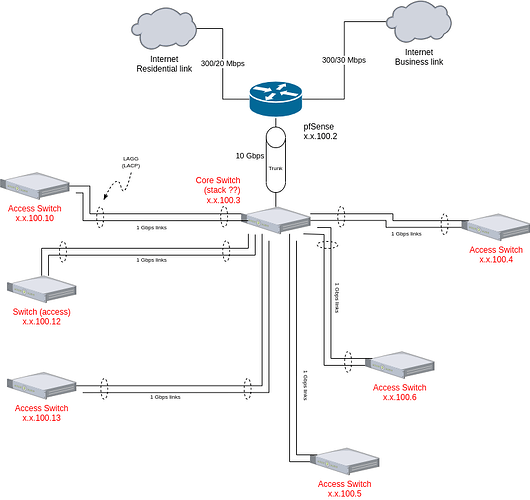
My pfsense box is setup with multiple WAN connections (Business class connection and residential connection), and multiple LAN connections (10G to house switch and 10G to AGG switch in garage).
As a note, I don’t have the AGG switch yet.
All of the ISP equipment and the majority of my network equipment will be in the garage. The switch in the house is directly connected to the pfsense box (LAN_House), and will connect to the AGG switch in the garage. All of my servers will also connect to the AGG switch, as well as a 48 port switch for the rest of the devices in the garage.
I route the traffic for my office via the Business Class (BC) gateway, and everything else over the residential (RES) gateway. I have several VLANs that are working well currently and I’d rather not give them up.
From what I’m reading and understanding, I have 3 possible ways to get both of the LAN connections working:
- Bridge the connections
- Use a different subnet on each interface and setup the DHCP server accordingly
- Setup a LAGG? not sure about this one, I don’t think it would serve my purpose.
What I am attempting to do, is to get both LAN_House and LAN_Garage interfaces to play nicely and still be able to use my VLANs. which that knocks #1 out of the situation.
Using a different subnet, I’m not opposed to… I would consider this like the classic “Cisco 5 router network” I’d have to figure out the IPs/subnets for each interface and the DHCP server, but then it would be a matter of setting up a static route between the 2 LAN connections, and then setup the VLANS on the other side, correct? I’m not sure on the VLAN aspect if that would work.
And honestly with the LAGG, I don’t think this will get me what I’m going for.
Please let me know if I’m missing something, or if there is a simpler/better option that would allow 2 LAN interfaces to either share an IP range or just act as one interface where VLANs can be used.
Thanks!