Hey guys!
So, I have a site (site1) where the topology is a sonicwall connected to a cisco switch handling DHCP/vlans then downstream I have my unifi enterprise switches, 4 total, and 6 u6 enterprise APs.
then next door to that site, I have another site (site2) Where i have a dedicated gig line going to a netgate 1541, then the comcast line for site1 also comes into that building and is just jumped next door with a cat6. Site2 has the same topology, except instead of a SonicWALL is the pfsense box.
I want to eventually do the same for site2, but for now i am just concentrating on site1. It makes no sense having 2 lines going into site 2, to then those lines be separated. So my plan is this:
on site1, remove the old crappy cisco switch doing DHCP/VLANs, remove the sonic wall and instead have just the pfsense do that. Then have the pfsense have redundant WAN.
so here is what the network looks like within the cisco switch:
ip dhcp pool ETHERNET
network 10.3.10.0 255.255.254.0
default-router 10.3.10.1
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
lease 7
!
ip dhcp pool VOIP_PHONES
network 10.3.20.0 255.255.255.0
default-router 10.3.20.1
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
option 160 ascii ftp://10.3.30.100
option 42 ip 10.3.30.100
option 2 hex ffff.aba0
!
ip dhcp pool Staff_SSID
network 10.3.40.0 255.255.255.0
default-router 10.3.40.1
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
lease 14
!
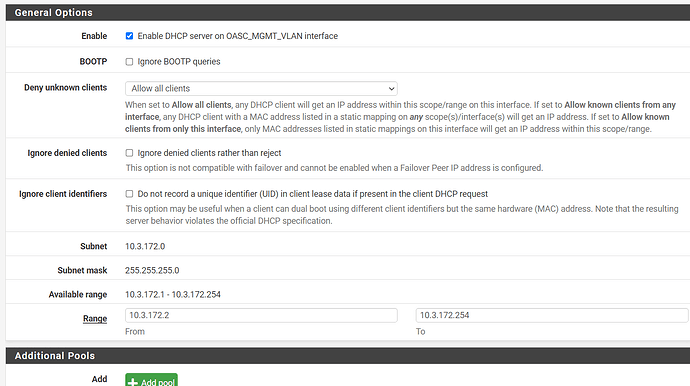
ip dhcp pool MANAGEMENT
network 10.3.172.0 255.255.255.0
default-router 10.3.172.1
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
!
ip dhcp pool SERVERS
network 10.3.30.0 255.255.255.0
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
default-router 10.3.30.3
!
ip dhcp pool GUEST_SSID
network 10.3.100.0 255.255.255.0
default-router 10.3.100.1
dns-server 10.3.30.100 10.3.30.100 208.67.222.222
lease 0 5
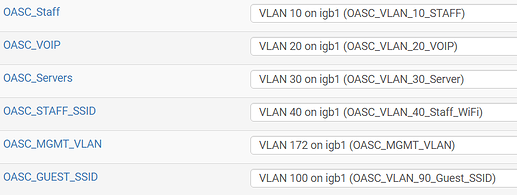
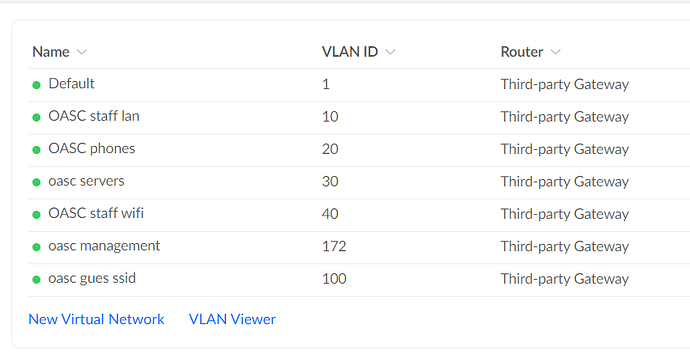
vlans:
interface Vlan1
no ip address
!
interface Vlan10
description STAFF_ETHERNET
ip address 10.3.10.2 255.255.254.0
!
interface Vlan20
description VOIP_PHONES
ip address 10.3.20.2 255.255.255.0
ip pim sparse-dense-mode
!
interface Vlan30
description SERVERS
ip address 10.3.30.2 255.255.255.0
!
interface Vlan40
description STAFF_SSID
ip address 10.3.40.2 255.255.252.0
!
interface Vlan100
description OASC_GUEST_SSID
ip address 10.3.100.2 255.255.255.0
!
interface Vlan172
ip address 10.3.172.2 255.255.255.0
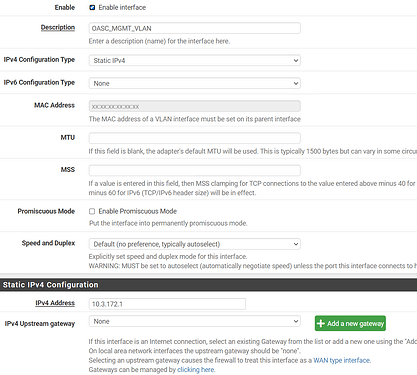
So easy enough to configure in PFsense, no issue. Just for testing, did a any/any rule on the vlans, configured the DHCP for the vlans to mimic the cisco switch then assigned the Vlans to an interface:
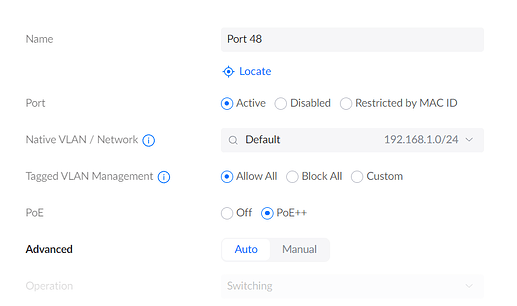
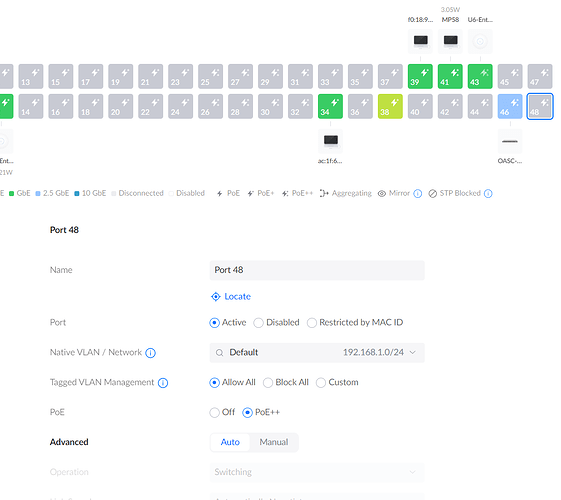
for the port where the pfsense would connect to my main unifi switch, is configured as such and all of them with DHCP (again just for testing, and make sure they get an IP address):
So when i go to connect the PFSense everything works, I see ARP entries for my phones, printers, etc. But for some reason, the Switches and APs do not get an address, i see no ARP entries for the 172 vlan at all and all unifi devices get stuck with the default 192.168.1.20 address.
I am sure i am missing something extremely simple, but any idea what could be? misconfiguration of the interface in the pfsense box? or something with my unifi switch?
Thank you guys for any help in advance!