Since the UTM is reaching EOL, I’m looking for a replacement but I haven’t found anything that is a direct replacement, that I can afford. This is for personal/home lab use but I do host quite a few things behind the device so I need the WAF, VPN, anti-virus, IPS, SMTP proxy, web protection etc. I’ve been utilizing most of the features of the UTM.
There must be some people on this forum that are very familiar with the Sophos UTM. Please tell me, can I replace the Sophos UTM’s functionality with pfSense, OPNsense or Untangle? I saw a post by Tom where he stated he usually pushes people towards Untangle when they need content filtering and WAF but Untangle doesn’t seem to have a reverse-proxy WAF. Outbound content filtering is not a huge concern for me as long as I can use URL lists and feeds but inbound inspection is very important to me.
It was several years back when I set everything up. Back then, not every connection was encrypted but now, all of my stuff uses HTTPS. The UTM’s IPS (Snort) catches a lot of things even with HTTPS traffic. This is what’s confusing me the most. I’ve read a lot of posts that state that IPS only works as man-in-the-middle and that you have to install a cert on all of the clients. I never installed any certs on the workstations or servers behind the UTM but I still see plenty of Snort blocked activity and false-positives in the WAF log so it must be working with HTTPS traffic, right? I’m referring to external traffic (443) coming into the UTM->WAF->internal webserver (80 or 443). The UTM’s WAF (reverse-proxy) handles the certs and port forwarding. So, is the UTM doing the man-in-the-middle thing by hosting the certs, accepting the HTTPS traffic and forwarding it to the internal web servers? Can I get the same functionality with *Sense or Untangle, with HTTPS traffic?
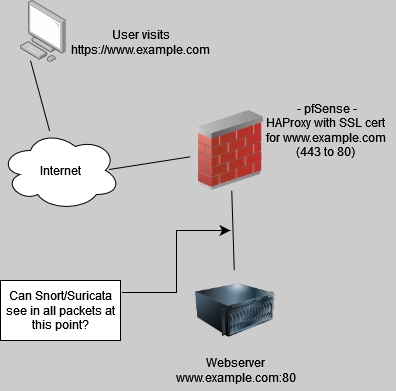
Contrary to what some may think, I have been searching my butt off trying to answer my own questions but I’m still confused. It looks like I may be able to cobble together all of the pieces with *Sense but it looks like a hot mess to me.
In Sophos UTM’s WAF, you can disable different Snort rules and add exceptions for each web app behind the UTM even if they are on the same interface. Based on the info I’ve obtained so far, it appears that pfSense only goes down to interface level. What about Untangle?
I would appreciate any advice including best practices if that means moving some of the functionality away from the firewall if it can be done reasonably well with open source in conjunction with *Sense or Untangle.