Perhaps someone has encountered the weird issues I’m facing ?
Background:
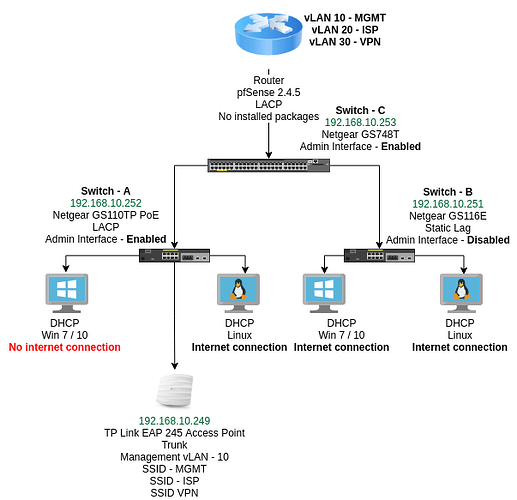
Have had my setup in place for nearly 2 years running without any major issues. All switches and access points are on a management vlan. Clients on any OS can connect to the internet and other vlans as defined by my rules.
Changes:
As part of my OCD I renumbered my management vLAN from 11 to 10, so all network switches and AP were renumbered from 11 to 10 subnet.
Result 1:
Lost access to my access point interface on 192.168.10.249 over the wired network. Did a factory reset. Still could not connect to the management interface.
If I connect to SSID-MGMT I can connect to the Access Point interface, Internet and devices on all vlans.
If I connect to SSID-ISP I can access the management interface, internet and devices on all vlans.
The access point is on a trunk with all vlans. The ethernet port I tried with both tagged and untagged but no luck.
Result 2:
Linux laptop can connect wired/wireless to the network with access to the network and all vlans.
Windows 7 & 10 laptop connects to the access point but fails to get internet access, when connected to switch A or C no internet access. However, when connected to switch B it has full internet and network access.
All my switches are Netgear, Smart Managed Pro, but Switch C is a Smart Managed Plus which means it’s still managed but with fewer features.
I discovered the Admin Interface was disabled on Switch C, however all the ports work. The Admin Interfaces on the other switches default to enabled, honestly I thought it was allowing access to the switch interface.
In my quest to solve this issue, I have ended up rebuilding pfSense 2.4.5 with a clean build along with factory resetting all switches except switch C.
If anyone has any clues it would be greatly appreciated 
The Windows machine that can’t connect to the internet, is that connected via the switch or AP?
Either way, I would troubleshoot all wired connections first and make sure that is good to go. Then you can work on the wireless. Since the wireless depends on the wired working properly you have to make sure that works first.
Yes the windows laptop is both wired and wireless. Wired works when connected to Switch B but nothing else.
Linux laptop works on wired and wireless, on all switches and access points.
My hunch is that there is an obscure setting on the switch which doesn’t like windows, though I have no idea which.
I’d research what “management vlan” means to your L3 switch. On some devices, it means that the interfaces that are a member of the management vlan will only accept tagged traffic for that traffic on that vlan. On other devices, this is configurable. So whatever connects to your switch on that vlan also needs to have their vlan tagging reconfigured to reflect the new vlan ID.
Yes you’re right @Kadarin however, Netgear are a bit sketchy in their documentation it’s tricky to find out how some of their features work or even what they are.
From my DD-WRT 30/30/30 days I decided to power down the network over night and this morning it was operating as I expected it to. My guess is that some of the vlan 11 settings hadn’t been totally removed. Don’t think that approach can be taken in an enterprise environment so there is probably a way to purge all settings from the switch that I need to know.
I totally agree that you shouldn’t have to power cycle a device to clear previous settings. I know some people aren’t friends of Cisco because of cost and the learning curve, but they have the best troubleshooting tools built in and I have had to deal with a similar thing before. I once had added a default route to a L3 switch and it took in the config, but not in the routing table. A quick check showed that and by removing the route and re-adding it the second time it took without a reboot. The reboot would have caused a complete outage for thousands of servers. Glad you get it working like you want! So what’s next?
Luckily this is just a home scenario, the funny thing is I had previously powered down the network but obviously impatience was my undoing, it needed a bit more time.
LOL I had wondered if I ought to upgrade to pfsense 2.5 this weekend as I like some of the new features in OpenVPN. This experience has shown me my documentation was miserable, even looking at previous settings I had no idea why I did what I did. I’m better off documentating for now, though I have noticed the network does feel snappy, so probably worth it.
The effect of using the CODEL limiters is pretty stunning, if I can get my head around some of the other algorithms I might be able to squeeze more performance … we’ll see.
1 Like
![]()