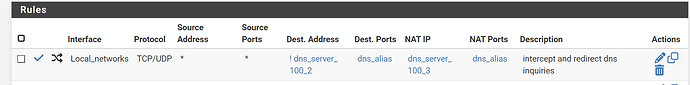
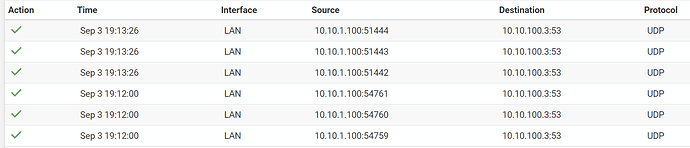
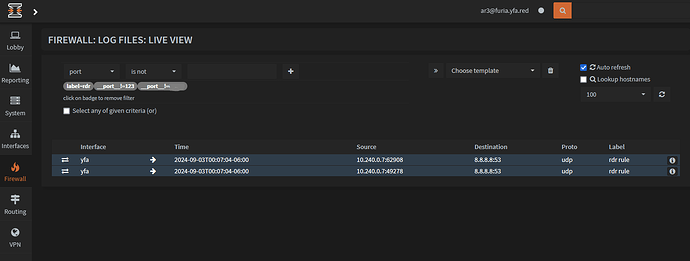
I’ve implemented a dns intercept as outlined in the pfsense recipe -
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
Local_networks = network group consisting of LAN and several VLANS
dns_server_100.2 = primary dns server (not pfsense)
dns_server_100.3 = 2nd ip on primary dns server
dns_alias = port 53 & 853
The forward is set up this way so that at least firewall rule logging could be done ONLY on the redirected traffic, otherwise due to firewall processing order, either all or none of the traffic (including that going to the 100.2 dns ip) would be logged.
The intercept works well, but I would like to actually know what the clients are trying to use for the original target dns address. With a firewall rule configured in the DNAT, resulting log shows the client IP and the 100.3 ip. I want to see the ORIGINAL target ip that triggered the DNAT in the first place.
Any thoughts? Thank you