I have a netgate appliance and was looking for a guide. I want to lock down my network with vlan’s while keeping functionality of iot devices.
I have never used VLANs and while I kind of understand how virtual lan’s work I still don’t know how best to set up my network according to my security concerns while not limiting use.
Is the strategy to have overlapping VLANs?
VLANs are more for network segmentation imo rather then network lockdown. To increase security for your network I would recommend limiting the acccess from vlan to vlan and general LAN access.
For segementation I would recommend to create VLANs for your Voice System, your normal Client LAN, your IoT Devices, your Server Network and DMZ. This would be a “basic” segmentation I would do and then go from there depending on your network size and needs.
Would a hub require being on the same VLAN as the IOT devices or would it be more secure to make a rule that allows the hub access to the IOT vlan? (The hub uses wifi devices that exist on the main wifi network as a remote). It’s a SOHO setup. Having more managed switch ports would make this easier but I am still fuzzy on where to draw the line.
Is there a tutorial for the “force pfsense DNS server” trick for the WAN?
Is this the best way to accomplish this on the wan?
pfSense Configuration Recipes — Redirecting Client DNS Requests | pfSense Documentation (netgate.com)Processing: BCnetwork.bmp…
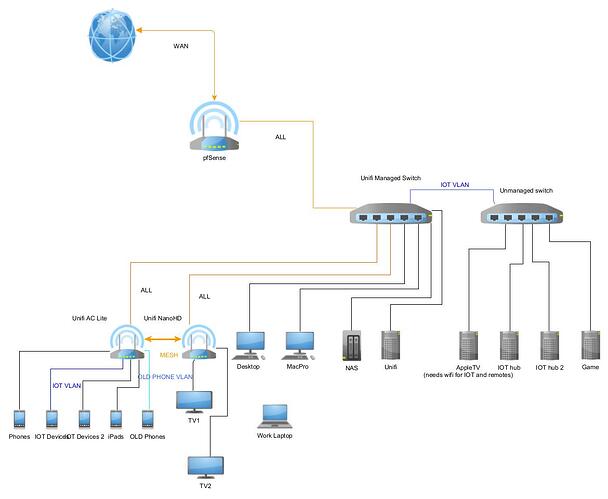
I posted a graph of the best case scenario for my network as I can see it.
Give your hub to charity and buy a managed switch. Then you can do as you wish.
Yeah I am seeing the old dumb switch as a major stumbling block now.
OK I just got more managed ports. I decided to go with something from the Ubiquiti store since shipping… is free?
Once I get the switch in hand I will try VLANs out. I am still a little confused how remotes will work over a vlan. I guess I should learn more about IOT before I try to manage it. Does all IOT traffic stay local or does it generally travel across the WAN?
So you have to define your objective / scope clearly. You want IOT devices to work with what resources exactly? What IOT devices specifically and what is the expected behavior? Some devices, you have no choice but to put on the same network for functionality (IE: Chromecast) without some fancy pants broadcast tricks. I would first identify which IOT devices you want to access what resources.
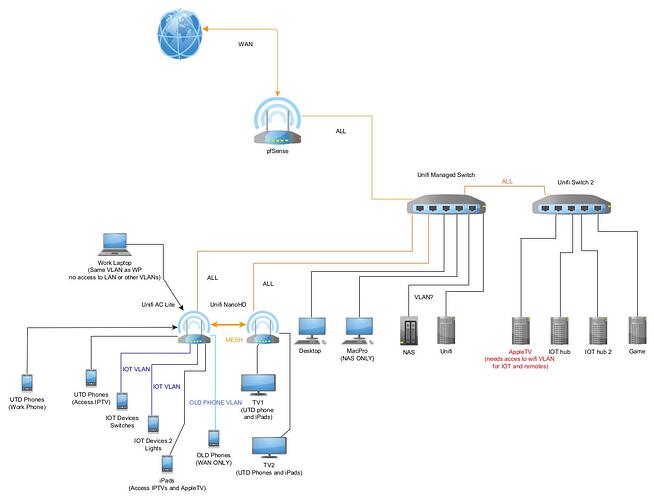
I will update the above network graph.
I need a few VLANs to accomplish what I want.
NAS
WORK
IOT
LAN
WAN ONLY
I think I need to put all the IOT devices on the same VLAN so they can broadcast messages to eachother. I am still unsure how to let the phones across the VLAN? Is that possible with firewall rules or do you need to use multiple VLANs for that?
Is there any benefit to assigning a device multiple VLANs? Is that even possible?
I have an alias with all my subnets. If I create an allow rule, all vlans can be accessed, denied, can’t access the vlans, invert, goes the WAN.
looking at aliases in the manual.
also found a LS video on the topic.
Everytbing @The_Other_Guy said is spot on.
I want to elaborate on dmz and vlan and servers/services.
I’m late, I know.
But for future readers.
The DMZ is typically created in three ways.
-
Physically using a single router with multiple physical WAN interfaces that get public IPs only and no lan. However, most people do not have de ices that support multi wan, and therefore rely on a single WAN with multiple LAN interfaces on different subnets.
-
Physically using multiple routers or layer 3 switching in a daisy chain or parallel. Again, typically using multiple WAN with public IPs only, however, it can be do e using the router or layer 3 switches LAN ports on different subnets.
-
Vrtually using vLans within a single lan interface.
Many vendors have their “in-house” way of enabling DMZ. No different than how UniFi makes implementing vlans easy, despite doing g it the “real” way is way more tedious with port tagging and so on.
The DMZ is used to place your servers outside your network but behind your WAF so if a service (http, sql, backend, etc) in the server is compromised and root or escalated privledges are had, there is no way for the intruder to gain access to any other lan or network segment.
Vlans with client isolation (clients cannot see other clients on the network, no discovery, snmp, broadcast limited) is best, since you will need to know the exact local IP address or WAN IP/FQDN to access the server(ers).
An intruder cannot see other servers on the network.
If there is a compromise the fix is easy, you can simply pull the server offline, kill the vlan on the router and switch, remake the vlan, and respin the server from a known good backup.
Always place your servers in a DMZ if you have public facing services. I.E your mine raft server, discord server, or website.
Otherwise for viewing your Webcam, logging I to your router, set up a VPN like wire guard or open vpn and VPN into your network instead of using their outward services. Unless the service provides the tunnel for you like unifi does for instance.
.
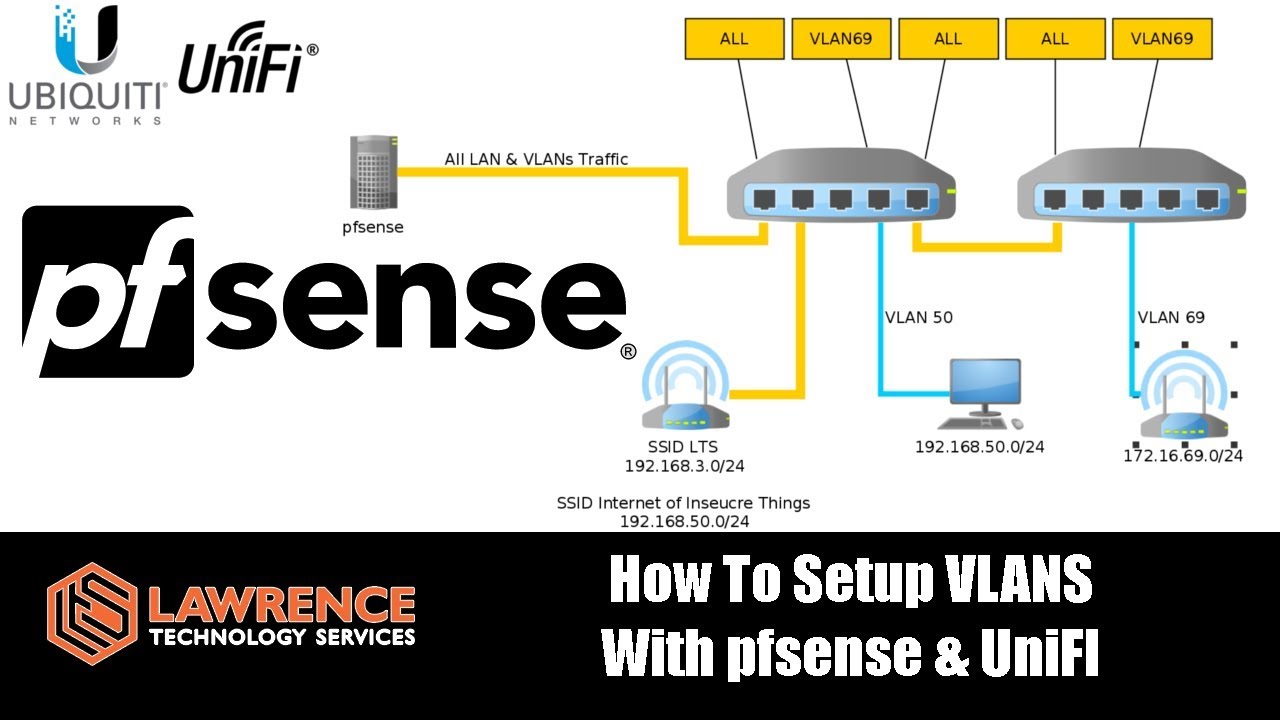
This video has been the best help for me to fully see how the entire process works.
OK I think I have a better understanding of how you configure the whole thing. I am now getting DNS entries on my firewall logs from the VLANs constantly so I am not sure everything is configured correctly as far as rules.(one was off)
I used aliases for my firewall rules but I stuck to the ones from the videos Tom discussed.
I moved my hub over to it’s own vLAN and it was really cranky and I lost all communication with it.
It was already late so I reverted it back to the original vLAN
Networking at home necessitates working by night.
pfsense and Rules For IoT Devices with mDNS - YouTube
This one too.
I am actually having issues with mDNS and a IOT device
Fixed it with avahi configuration. Must have had deselected things somehow.
Edit: Nevermind some IoT devices no longer respond to the controller.
I looked at the advice of a few other people who suggested IGMP snooping and other ports being opened but after comparing them to the current rules I realized none of that was necessary. I realized I may be misattributing the failure to the rules and vlans. I rebooted the controller for these devices again and everything is working now.
Great guides for doing this for your network. Thanks a lot Tom and all.