I am inexperienced in using PFsense and the Netgate SG-3100, but trying to learn. Recently installed two Ubiquiti UAP-AC-Pro access points on my network.
I have IPv6 disabled yet there are hundreds of blocked IPv6 traffic records originating on my LAN in my firewall logs every hour.
Also, why would my Ubiquiti Access Points show up in my firewall block logs as the source of some (24%) of blocked IPv6 traffic? Does the Unifi controller use IPv6 on the LAN?
What are the addresses? Do they start with fe80? When you say that IPv6 is disabled I am going to assume you mean the “allow IPv6” checkbox in system > advanced > networking is unchecked. But keep in mind that if DHCPv6 is enabled your devices may still be getting addresses and trying to reach the internet. Overall it’s nothing to worry about, but you should probably turn off services you don’t use. Which firewall rule is blocking this traffic? Logging is not usually turned on for the default blocking rules. I hope this helps.
Thank you for your response and ideas.
Almost all of internal addresses do begin with fe80.
The allow IPv6 box is unchecked.
The DHCPv6 server is not enabled.
The rule that is blocking is the default deny IPv6 rule.
I looked at the rule, how do I turn off the logging?
My installation was guided by Tom’s PF sense installation video, so I think there should not be any extra services.
Just curious why there would be so much internal IPv6 traffic?
Those default block rules will be pretty noisy so turning off logging is good. It’s down toward the bottom of the rule under “extra options”. If you need a rule to catch blocked connections for troubleshooting I have found it helpful to log TCP packets with the SYN flag set (both TCP flag SYN checkboxes in the advanced options) right above that default block rule. Of course that only works for TCP connections, but it’s pretty helpful non the less.
As for why there is so much IPv6 traffic. SLACC! The short story is that devices can assign themselves addresses and try and communicate without the need for DHCPv6. So even if your router doesn’t route the traffic (such as if the IPv6 gateway disabled) or your firewall blocks it as you are seeing now, they can still communicate directly on the switch if they are on the same VLAN.
I have two Ubiquiti access points and a Unifi controller running on a desktop on my network. Maybe they are the source of this traffic…….
Do you have IPv6 enabled on the networks in your Unifi controller? This is found in the settings > networks > edit a network then scroll down to IPv6 and look for an option to set IPv6 to none. Also see the NDP table in pfSense for a list of what it has discovered.
You wont see IPv6 addresses in Unifi under the clients tab unfortunately. On a small home network it might be faster to get on each client one at a time and look at the IP info. I wouldn’t worry about it though, it’s just normal IPv6 noise.
I checked the unifi controller and found the IPv6 was not enabled. I spent some time looking at the traffic and some of the blocked IPv6 addresses and found that some of them(24%) were the Ubiquity AP’s.
I went through my rules. There are not many. 2 WAN, 3 Lan, and 2 floating. Logging was not an option or was not checked on any of them except one created by PF blocker. I removed the logging check mark on this rule, but it did not change the quantity of blocked IPv6 in the logs. Only one of the rules is explicity identified as IPv6, but it’s logging is unchecked.
I checked a router at one of my client’s sites who actually uses IPv6 for some IoT stuff and there is no noise in their logs either. On the internal interfaces (interfaces > LAN for example) IPv6 configuration type is set to none for all of the interfaces where we don’t want IPv6. WAN is set to DHCP6, and the internal interface where we “need” IPv6 is setup per their ISP’s instructions (track interface in this case). If you are going to have IPv6 enabled on an internal interface you need to take a close look at how you are doing router advertisements (services > DHCPv6 Server & RA > router advertisements). I believe the default is assisted mode but I may be wrong, I didn’t look.
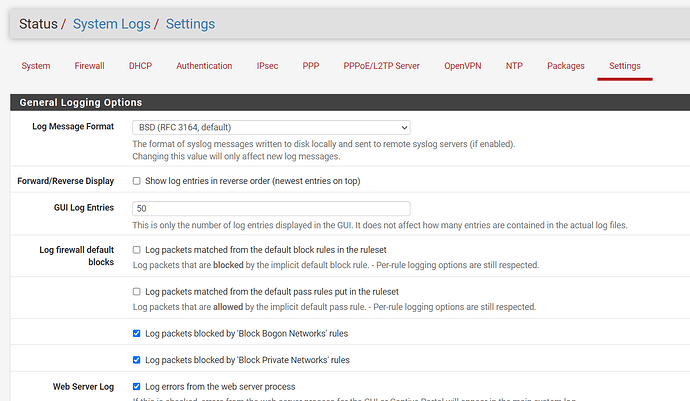
In pfSense in Status > system logs > settings you may want to take a look at the “Log firewall default blocks” section. I have the first two unchecked on mine, but those are match rules that make a lot of noise.
I unchecked the first two rules as you recommended a few days and havent had any block log entries since then. It does appear that nearly all of the traffic is internal and likely SLAAC related as you suggested. I hate to turn off logging, but the massive of amount of data wasn’t useful at all. I looked at a recent sample of 10,000 log entries, and it occurred in just over 6 minutes. Thank you for your assistance!
Glad I could help! The most important thing about logging is that the data generate is useful. If the haystack is so big you cant find the needle then the logs are worthless. Have a great day!