Hi, thanks for taking the time to reply…
Today I discovered something which I thought might have been the issue. While it definitely was a breaking issue, it probably only was another non working piece.
So, I do have a dynamic DNS and pfSense is updating that at Cloudflare … or so I thought. It actually did for a while but for security reasons I replaced the global Cloudflare API key with a custom API key which is restricted to DNS changes for a specific zone only. However, that doesn’t seem to work properly, at least not with pfSense and the updates failed. I now swapped back to the global key and the updates work again and then I flushed all my DNS caches.
As a sidenote, on another system somewhere else I use the custom key in a script and it does work fine.
Regarding Let’s Encrypt certs and TXT record, I don’t think a TXT record is required since I use the Cloudflare API for that.
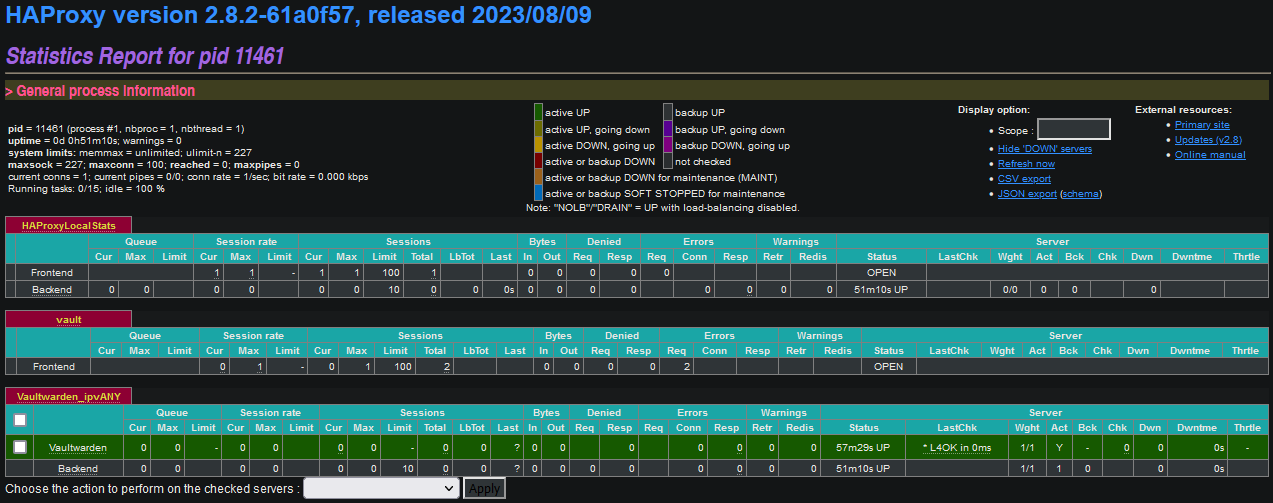
Here is a screenshot of the HAProxy STATS page.
I only have 1 Frontend defined currently. I only use 1 level subdomains like vault.domain.nz
Current HA Proxy config:
<haproxy>
<ha_backends>
<item>
<name>vault</name>
<descr><![CDATA[vault.mydomain.nz]]></descr>
<status>active</status>
<type>http</type>
<httpclose>http-keep-alive</httpclose>
<ssloffloadcert>65beb4eec8e44</ssloffloadcert>
<ssloffloadacl_an>yes</ssloffloadacl_an>
<advanced></advanced>
<ha_acls>
<item>
<name>vault</name>
<expression>host_matches</expression>
<value>vault.mydomain.nz</value>
<backendservercountbackend>Vaultwarden</backendservercountbackend>
<_index></_index>
</item>
</ha_acls>
<ha_certificates></ha_certificates>
<clientcert_ca></clientcert_ca>
<clientcert_crl></clientcert_crl>
<a_extaddr>
<item>
<extaddr>wan_ipv4</extaddr>
<extaddr_port>443</extaddr_port>
<extaddr_ssl>yes</extaddr_ssl>
<_index></_index>
</item>
</a_extaddr>
<a_actionitems>
<item>
<action>use_backend</action>
<acl>vault</acl>
<use_backendbackend>Vaultwarden</use_backendbackend>
<_index></_index>
</item>
</a_actionitems>
<a_errorfiles></a_errorfiles>
</item>
</ha_backends>
<ha_pools>
<item>
<ha_servers>
<item>
<status>active</status>
<name>Vaultwarden</name>
<address>192.168.1.30</address>
<port>7011</port>
<id>101</id>
<_index></_index>
</item>
</ha_servers>
<a_acl></a_acl>
<a_actionitems></a_actionitems>
<errorfiles></errorfiles>
<advanced></advanced>
<advanced_backend></advanced_backend>
<name>Vaultwarden</name>
<balance></balance>
<balance_urilen></balance_urilen>
<balance_uridepth></balance_uridepth>
<balance_uriwhole></balance_uriwhole>
<transparent_clientip></transparent_clientip>
<transparent_interface>lan</transparent_interface>
<check_type>Basic</check_type>
<checkinter></checkinter>
<log-health-checks></log-health-checks>
<httpcheck_method>OPTIONS</httpcheck_method>
<monitor_uri></monitor_uri>
<monitor_httpversion></monitor_httpversion>
<monitor_username></monitor_username>
<monitor_domain></monitor_domain>
<monitor_agentport>Vaultwarden</monitor_agentport>
<agent_check></agent_check>
<agent_port></agent_port>
<agent_inter></agent_inter>
<connection_timeout></connection_timeout>
<server_timeout></server_timeout>
<retries></retries>
<stats_enabled></stats_enabled>
<stats_username></stats_username>
<stats_password></stats_password>
<stats_uri></stats_uri>
<stats_scope></stats_scope>
<stats_realm></stats_realm>
<stats_admin></stats_admin>
<stats_node></stats_node>
<stats_desc></stats_desc>
<stats_refresh></stats_refresh>
<persist_stick_expire></persist_stick_expire>
<persist_stick_tablesize></persist_stick_tablesize>
<persist_stick_length></persist_stick_length>
<persist_stick_cookiename></persist_stick_cookiename>
<persist_sticky_type>none</persist_sticky_type>
<persist_cookie_enabled></persist_cookie_enabled>
<persist_cookie_name></persist_cookie_name>
<persist_cookie_mode>passive</persist_cookie_mode>
<persist_cookie_cachable></persist_cookie_cachable>
<persist_cookie_postonly></persist_cookie_postonly>
<persist_cookie_httponly></persist_cookie_httponly>
<persist_cookie_secure></persist_cookie_secure>
<haproxy_cookie_maxidle></haproxy_cookie_maxidle>
<haproxy_cookie_maxlife></haproxy_cookie_maxlife>
<haproxy_cookie_domains></haproxy_cookie_domains>
<haproxy_cookie_dynamic_cookie_key></haproxy_cookie_dynamic_cookie_key>
<strict_transport_security></strict_transport_security>
<cookie_attribute_secure></cookie_attribute_secure>
<email_level></email_level>
<email_to></email_to>
<id>100</id>
</item>
</ha_pools>
<configversion>00.58</configversion>
<files></files>
<email_mailers></email_mailers>
<dns_resolvers></dns_resolvers>
<maxconn>100</maxconn>
<logfacility>local0</logfacility>
<loglevel>debug</loglevel>
<localstatsport>2200</localstatsport>
<nbthread></nbthread>
<hard_stop_after></hard_stop_after>
<localstats_refreshtime></localstats_refreshtime>
<localstats_sticktable_refreshtime></localstats_sticktable_refreshtime>
<log-send-hostname></log-send-hostname>
<ssldefaultdhparam>2048</ssldefaultdhparam>
<email_level></email_level>
<email_myhostname></email_myhostname>
<email_from></email_from>
<email_to></email_to>
<resolver_retries></resolver_retries>
<resolver_timeoutretry></resolver_timeoutretry>
<resolver_holdvalid></resolver_holdvalid>
<terminate_on_reload></terminate_on_reload>
<sslcompatibilitymode>intermediate</sslcompatibilitymode>
<enable></enable>
</haproxy>
A remote Linux system returns correct IP when doing a dig or ping on vault.mydomain.nz.
When I try openssl s_client -servername vault.mydomain.nz -host 123.123.123.95 -port 443 I get a timeout though.
A local Linux can ping vault.mydomain.nz which resolves to pfSense’s IP address (192.168.1.2) as defined in the DNS resolver. (that same IP is also the Linux’ only DNS server in resolv.conf).
Running openssl s_client -servername vault.mydomain.nz -host 123.123.123.95 -port 443 on the local Linux does return a certificate.
That seems like pfSense/HAProxy is not serving or answering requests from WAN which makes me wonder if something is wrong with my firewall rules but my WAN rules are pretty simple:
<rule>
<id></id>
<tracker>1708120689</tracker>
<type>pass</type>
<interface>wan</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<protocol>tcp</protocol>
<srcmac></srcmac>
<dstmac></dstmac>
<source>
<network>wanip</network>
</source>
<destination>
<network>(self)</network>
<port>80</port>
</destination>
<descr><![CDATA[HAProxy HTTP]]></descr>
<bridgeto></bridgeto>
<updated>
<time>1708120689</time>
<username><![CDATA[admin@172.16.16.8 (Local Database)]]></username>
</updated>
<created>
<time>1708120689</time>
<username><![CDATA[admin@172.16.16.8 (Local Database)]]></username>
</created>
</rule>
<rule>
<id></id>
<tracker>1708120727</tracker>
<type>pass</type>
<interface>wan</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<protocol>tcp</protocol>
<srcmac></srcmac>
<dstmac></dstmac>
<source>
<network>wanip</network>
</source>
<destination>
<network>(self)</network>
<port>443</port>
</destination>
<descr><![CDATA[HAProxy HTTPS]]></descr>
<bridgeto></bridgeto>
<updated>
<time>1708120727</time>
<username><![CDATA[admin@172.16.16.8 (Local Database)]]></username>
</updated>
<created>
<time>1708120727</time>
<username><![CDATA[admin@172.16.16.8 (Local Database)]]></username>
</created>
</rule>
Only have 1 floating rule which only affects another interface.
Does this give away any clues?
CHeers