Hi, I always see vlan 1 as management vlan and 4091 as LAN vlan tags. But as a security measurement, 1 is not really allowed.
So how can I change this or what should I do to remove the threat? And how can I change vlan 4091 tag to another number?
I’m not really sure what your question is. You have already identified that you don’t want to use VLAN 1 due to security concerns. So… just don’t use it then. You are free to choose any VLAN you like. How you change it depends on the gear you’re using.
Well, I am a noob in this…
But the 1 IS in use by the management vlan? Whatever that may be.
If a switch is connected to the Netgate, it is connecting because of both have vlan 1 , no?
So a “hacker” can connect his switch to the network as well? Or has this got nothing to do with it?
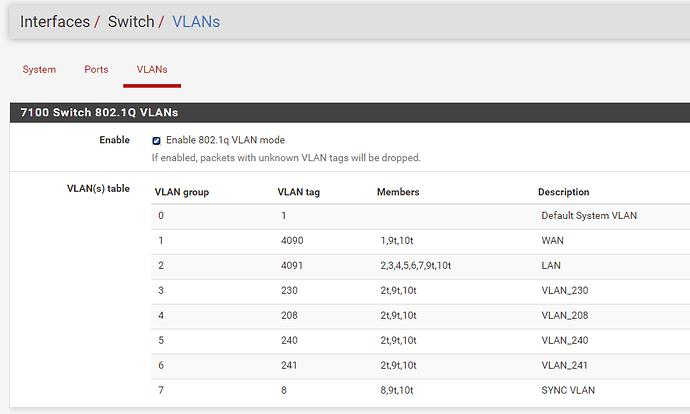
Also my chief wants the devices with static ip’s to be in the 192.2.50.0 range. The Netgate has 192.2.50.253. But it is in the default 4091 vlan. How can I safely change this to a tag 250?
This is what it is now.
4090 and 4091 are internal use tags for their internal use not exposed exposed externally.
So I ignore the question about “removing/disabling” vlan tag 1 and 4091 then.
But on the switches I’ll have to make vlan tags 4091, 230, 208, 240,… and remove vlan tag 1 ? Or … ?
No, ignore 4091 as it does not leave the device. And if you don’t want to use VLAN 1 (native) then don’t.
Ok, but the Netgate device has ip 10.2.50.253, and the DHCP is 10.2.50.1-250 (this is a HA device as well) , so basically to keep it neat this vlan should be a vlan with tag 250. and on the switch I could put ports open only for port 250.
and another port is then used only for vlan tag 230.
Or actually all ports should be open to vlan tag 250 I pressume as otherwise they cannot reach devices in vlan tag 250. (Or is this something that should be done in the Firewall rules of that vlan?
Or, if I really want to have a vlan_250, should I put the Netgate in eg 10.2.10.0 and create a separate vlan 250 where I stack all the device which I want in vlan 250?
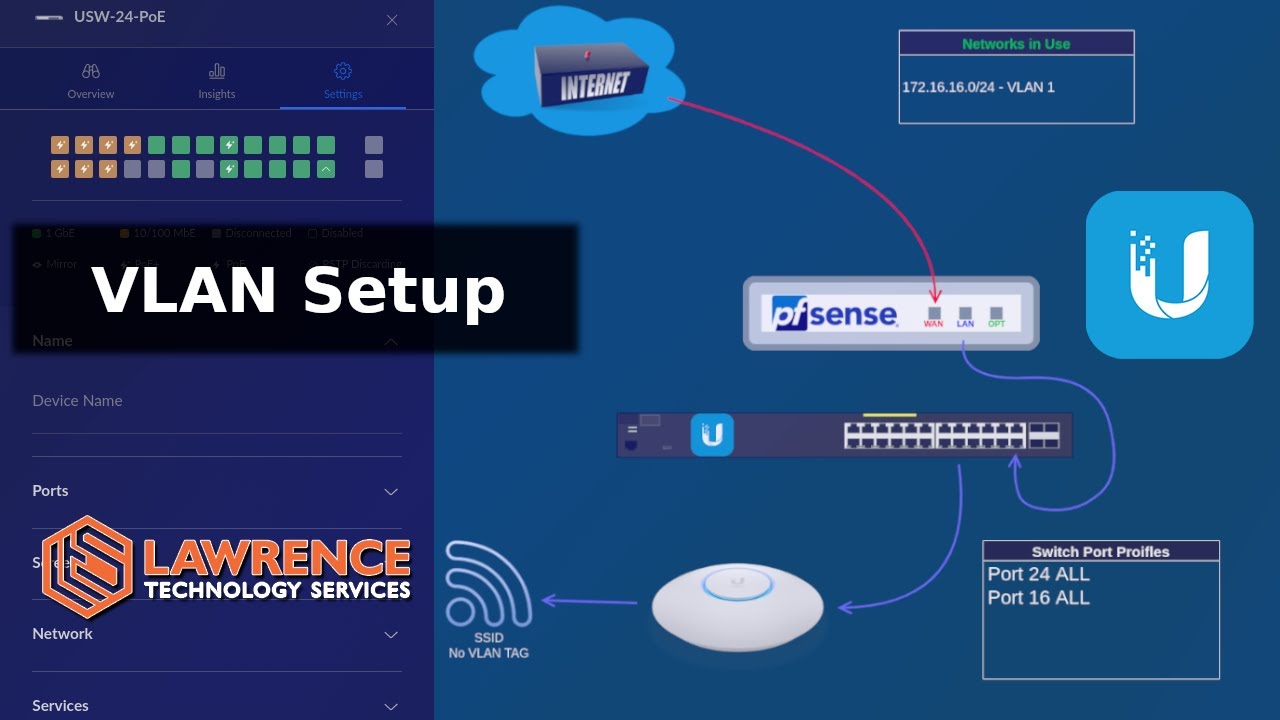
I am not completely clear on what you are asking, but I do have a 2022 video that covers VLAN & pfsense using UniFi, but it could be applied to what ever switch you are using.
Yes, I have seen it. But you use VLAN 1 in it, and for security reasons that is apparently not a good idea?
My setup is being used in a secure lab environment where all vlans will only be on there own vlan, except they have access to vlan 250 and vlan 230 (as these are devices like NAS or Server) , some vlans are even not allowed to the internet.
The security issue is that VLAN 1 can see the traffic of the other VLANs if you do not strip the other tags from the ports. Security comes down to how you configure things.
OK, so how should I go on with this then?
Follow my video, don’t use VLAN1 native.
Hello Tom.
I have a similar situation where if I can avoid using VLAN 1, it would be great! I am building a new UNIFI network and I have a on-premise UNIFI controller with about 12 different switches. There is a bit of a chicken and egg issue at least in theory. The “first” switch I am provisioning would be a POE 48 port “server” switch which is directly connected to the controller.
I suppose the direct question would be… Can you add the management VLAN within the VLAN database of the first switch and configure the port connected to the controller to the same MGT vlan? Then adopt the switch and controller? My concern is the controller will wipe any custom configuration during the adoption phase.
You can not configure the switches before adopting them.