On this topic I think that adversaries have other avenues besides Shodan that I wanted to highlight here.
I work as a software developer for a pharmaceutical company in USA and have a LinkedIn account that shows the name of this company and some of my other (rather standard level) detail.
Some weeks back I received a connection request from someone named Derek Perry who is (purportedly) a web developer working for Fluor Corp. I knew of the Fluor Corporation since previously because of doing some small scale stock trading in the past and as part of this had researched the company. So on the surface it seemed like an OK connection request although I had never met the guy before.
Now I know that some people only connect with those whom they have met in real life. And that there are those who are willing to connect with people whom they have not met, just in order to grow their own network. I thought that perhaps this Mr Perry was one of the latter.
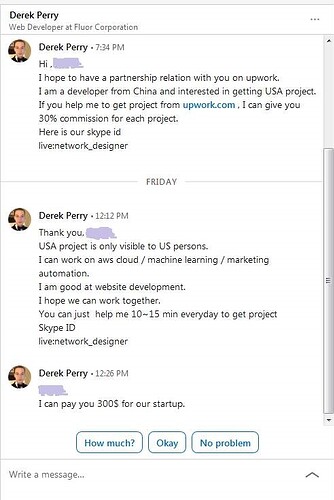
Anyway so after accepting the connection I received some requests (shown in the image attached here) from this connection, asking that I help him to get gigs at upwork. He requested that we handle the communication on Skype.
The way that he wrote (for example referring to “our” skype id) gave me a feeling that he represented some group of people.
So I spent some time contemplating about how to reply to him. It could be that I have become a bit too paranoid because of handling sensitive systems at my employers company (and having dealt with a couple social networking attacks previously) but I ended up reporting the connection to LinkedIn due to that sort of concerns.
There is always a risk for some information leakage when dealing with strangers who know where you work. Sites like LinkedIn can provide a source of “massageable resources” in those cases where Shodan does not find anything…