Disclaimer: I do not use UniFi equipment and my SSL offloading experience comes from using Netscaler devices. So let me ask you some more general questions to fully understand your question):
What is your ultimate goal here? Traffic designed to go to the Unifi Controller is getting an ssl cert error and you want to fix that? What is the specific cert error you are getting? Narrowing it down to that, let’s drill down:
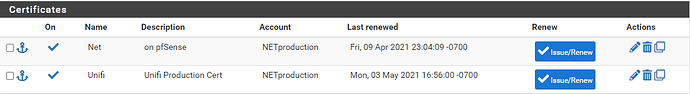
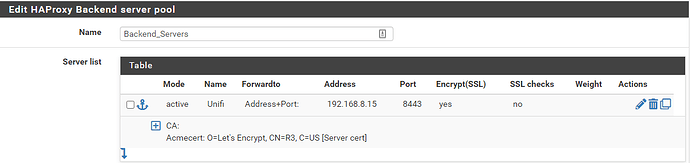
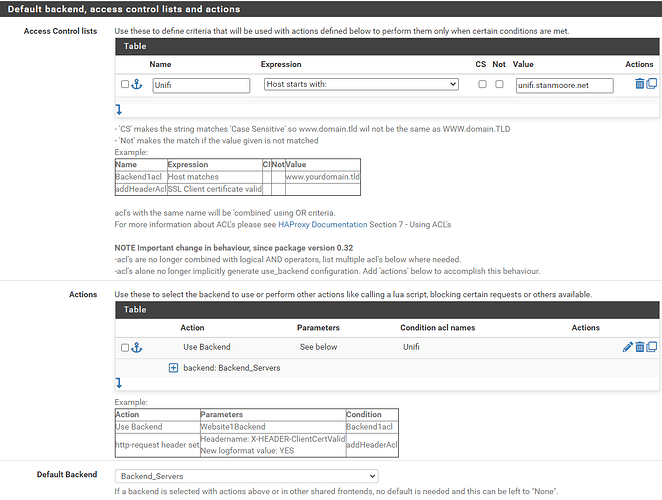
You have a Proxmox server that has created a LXC container, which for you is running the UniFi Controller software, and it has an ip of 192.168.8.15. Per the Edit HAProxy Backend server pool shot, it’s listening on tcp port 8443. And no, Proxmox is not enforcing backend checks on the backend cert (not really needed for a home env.) Nothing at all wrong here.
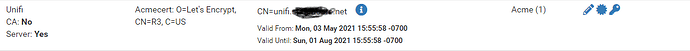
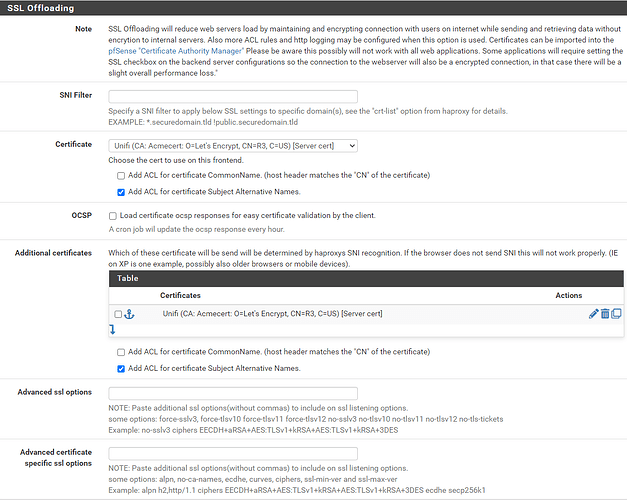
You want to use the on pfSense cert, not the Unifi Production Cert, correct? Or vice versa?
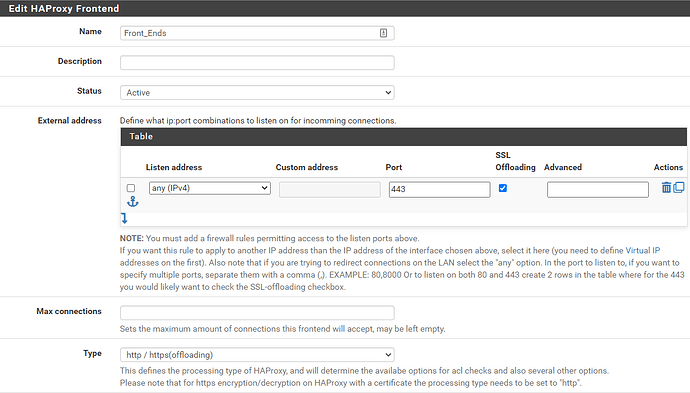
Will clients be connecting to port 443 or 8443? Per your “front ends” screenshot, you have it set to port 443 ONLY. Is your intention to have clients connect on 443 and get forwarded to port 8443 on the backend?
For certificate trust to work, the Let’s Encrypt server cert you got needs to be linked to the CA that issued you that cert. On a netscaler, that would be a command like "link ssl certKey " where a “certkey name” is a label that refers to a matching cert/key pair, so “link ssl certkey mycervercert LetsEncryptCAcert”. Proxmox has to have equivalent functionality there, and it may be as simple as downloading the CA cert to your Proxmox and linking the two in order to fix your entire problem.
One final note: If you’re using your server cert to host multiple domains, you have a choice of using SANs or SNI.
SNI (Server Name Indication) is where the SSL Client Hello offers in cleartext to the server which particular domain it intends to connect to, and SNI directs the traffic for the appropriate domain.
SAN (Subject Alternative Names) is where the Client Hello does NOT do the above. The cert instead has a list of domain names for which it is responsible. If your domain name is on the list, great. If not, you should get an error in your browser. While it may look similar, it’s not the same error as the trust issue above
On any linux host with openssl on it, do a “openssl x509 -in yourcertfile.crt -text -noout” and that’ll give you the CN and SANs that you added to the original cert request you made, so you can verify that what you want is there.