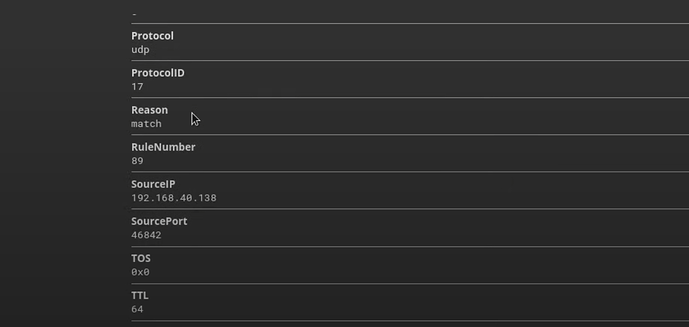
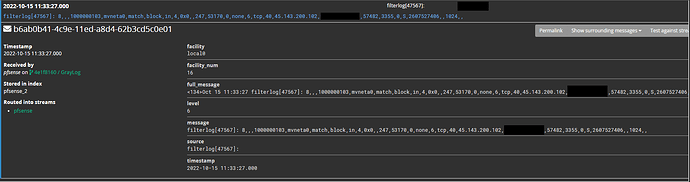
Hope this helps, here are my current extractors:
{
"extractors": [
{
"title": "pfSense filterlog: IPv4 TCP",
"extractor_type": "regex",
"converters": [
{
"type": "csv",
"config": {
"trim_leading_whitespace": false,
"column_header": "RuleNumber,SubRuleNumber,Anchor,Tracker,Interface,Reason,Action,Direction,IPVersion,TOS,ECN,TTL,ID,Offset,Flags,ProtocolID,Protocol,Length,SourceIP,DestIP,SourcePort,DestPort,DataLength,TCPFlags,Sequence,ACK,Window,URG,Options",
"strict_quotes": false
}
}
],
"order": 1,
"cursor_strategy": "copy",
"source_field": "message",
"target_field": "FilterData",
"extractor_config": {
"regex_value": "^filterlog\\[.+\\]:(.+)"
},
"condition_type": "regex",
"condition_value": "^filterlog\\[.+\\]:(.+),(in|out),4,.*,tcp,.*$"
},
{
"title": "pfSense filterlog: IPv4 UDP",
"extractor_type": "regex",
"converters": [
{
"type": "csv",
"config": {
"trim_leading_whitespace": false,
"column_header": "RuleNumber,SubRuleNumber,Anchor,Tracker,Interface,Reason,Action,Direction,IPVersion,TOS,ECN,TTL,ID,Offset,Flags,ProtocolID,Protocol,Length,SourceIP,DestIP,SourcePort,DestPort,DataLength",
"strict_quotes": false
}
}
],
"order": 2,
"cursor_strategy": "copy",
"source_field": "message",
"target_field": "FilterData",
"extractor_config": {
"regex_value": "^filterlog\\[.+\\]:(.+)"
},
"condition_type": "regex",
"condition_value": "^filterlog\\[.+\\]:(.+),(in|out),4,.*,udp,.*$"
},
{
"title": "pfSense filterlog: IPv4 ICMP",
"extractor_type": "regex",
"converters": [],
"order": 0,
"cursor_strategy": "copy",
"source_field": "message",
"target_field": "FilterData",
"extractor_config": {
"regex_value": "^filterlog\\[.+\\]:(.+)"
},
"condition_type": "regex",
"condition_value": "^filterlog\\[.+\\]:(.+),(in|out),4,.*,icmp,.*$"
}
],
"version": "4.3.8"
}