| Features | pfsense | Untangle | USG/USG-Pro | UDM/UDM Pro | EdgeRouter |
|---|---|---|---|---|---|
| Operatins System | BSD | Linux | EdgeOS / UniFi SDN | UniFi SDN | EdgeOS / UNMS |
| Centralized Management | no | Yes | Yes | Yes | Yes |
| OpenVPN Server | Yes | Yes | Yes (via command line) | Yes (via command line) | Yes (via command line) |
| OpenVPN Client | Yes | Yes | Yes (via command line) | Yes (via command line) | Yes (via command line) |
| IPsec | Yes | Yes | Yes | Yes | Yes |
| L2TP VPN | Yes | Yes | Yes | Yes | Yes (via command line) |
| Policy Routing | Yes | yes | Yes (via command line) | Yes (via command line) | Yes (via command line) |
| IDS/IPS | Suricatia or Snort | Suricata | Yes | Yes | no |
| DNS Filtering | pfblocker | yes | no | Beta Feature | no |
| GeIP Filtering | pfblocker | yes | no | Beta Feature | no |
| Web Content Filtering | squid | yes | no | no | no |
| QoS / Traffic Shaping | advanced | advanced | basic | basic | Yes (via command line) |
| WAN Failover | Yes | Yes | Yes | UDM Pro | Yes |
| Load Balancing WAN | Yes | Yes | Yes | UDM Pro | Yes (via command line) |
| Active Directory Intergration | No | Yes | No | No | No |
| Captive Portal | Yes | Yes | Yes via SDN Controller | Yes via SDN Controller | No |
| Let’s Encrypt Certificates | Yes | No | No | No | No |
| HA Proxy | Yes | No | No | No | No |
Firewall Feature Comparison 2020: pfsense, Untangle, USG, Dream Machine, UDM Pro, & EdgeRouter chart
For the UDM, everything that you have as “via command line”, to my understand should be “No”. While there are some things you can do via command line on the UDM, almost everything is wiped on restart. I am even less interested in doing anything outside the SDN on the UDM than I ever was with USG.
I think the Load Balancing WAN for the USG should be “via command line” - at least every time I see someone setting up load balancing on the USG they’re doing it from there. Also on the UDM Pro, Load Balancing isn’t yet available, since it isn’t in the UI. You also can’t select the SFP+ as WAN1/Primary, it is always Secondary.
Maybe this isn’t something you deal with, but I would personally have put into this spreadsheet “Able to disable NAT”. The answers would be:
Yes
(I don’t personally know, assuming yes)
Yes (via command line)
No
(I don’t personally know, assuming yes)
Edit: The reason I would personally include this is that many people would like to have a USG or UDM in the network, but use something above it for the routing functionality. Personally I would have a Mikrotik above it. In a real-world scenario, I can show you hundreds of large, big-name hotels that have a Nomadix gateway with NAT disabled, and the NAT/routing being done by a Watchguard firewall. It is the preferred deployment of a certain industry leading MSP ![]()
EDIT2: Would you accept additions from trusted/vetted individuals? I understand fully that you might want to only have your and your company’s name attached to information you have determined yourself.
We can discuss this here and I will update the sheet. And I agree the that just because you can edit from the command line certainly does not mean you should with the UDM / USG devices. I also had more features on the sheet, but I realized it would have made the video a whole lot longer. Overall I don’t mind doing a part two discussing more advanced features.
Tom, I think you may have undersold the edgerouter, you can do most of the CLI stuff through the config tree on the right hand side of the edge router UI(I’ve used it for setting up openVPN) . Not only that, but there is a whole tab for QOS and a wizard for load balancing.
They are very capable as routers and support many advanced routing features and protocols(bgp,ospf, and rip for starters, which the USG does not support via GUI), but as a firewall are restricted to ACL based rules, and don’t support advanced features in this respect.
I know and I am not denying the EdgeRouter has a lot of features, but even per their official documentation, they require command line configuration for most advanced functions. While I don’t have an issue with doing command line work myself, it does require a bit more learning than using a web interface making it harder to have a team that can support it. By comparison, pfsense offers all these options via their web interface. A big reason for this video was the number of techs setting small offices who go out and buy an EdgeRouter or USG and want the same functionality with services that are integrated into pfsense and Untangle and realizing they are not as simple to deploy. If you are going by price alone, EdgeRouters and even MikroTik offer an excellent value / features ratio, but both of those devices have steeper learning curves.
A Part 2 sounds inevitable anyway since at some point the number of changes fron what you presented would become significant enough to warrant a “2021 update” or whatever.
I know you’re looking at the UDM Pro, but based on what I’ve read on UI’s forums and Discord, I think you should at least wait for 1.6.5 to be released - allegedly that will happen this week or next week. There’s a number of fixes that have been promised in that update, for some people 1.6.4 is very broken. The product may be released to GA but the software is very much not ready yet.
Curious seeing that pfsense has no central / remote management built in. What is the preferred method for remote / bulk management?
I am guessing that setting up a vpn would be the method, but wondering is this the most preferred.
Tom, Thats fair. They all have seemingly very different purposes.
Thedannymullen, that’s how I currently connect to my networks.
They can be managed remotely via VPN, or SSH+ProxyChains, or by opening up web interface on WAN filtering for only certain public IP’s.
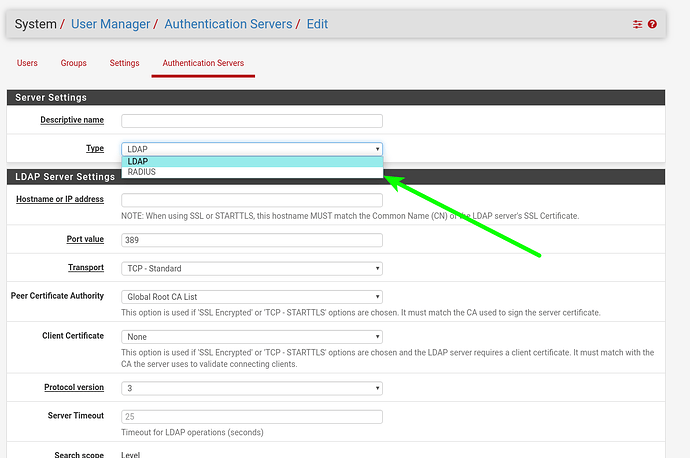
pfsense is listed with no Active Directory integration. That’s incorrect. I’m running 2.4.4 and I’ve had my config integrated with AD for quite some time. The option is listed under User Manager > Authentication Servers
I would be nice however if pfsense did have one centralized remote management hub however. Perhpas this is a niche case since each LAN is different but it would be nice to have a “global config” which you could make changes to a bunch of machines all at once and then possibly ssh/http into each invidual router to customize.
For pfsense: LDAP is a way of speaking to Active Directory, but LDAP is not the same as having straight AD authentication.
Tom - you had mentioned Meraki in the vid and I think I MUST throw in my $.02. Meraki’s VPNs are made for pretty much one thing, and that’s site to site using larger than /32s (I think /24s are a minimum), and certainly are not capable of limiting non-sequential IPs on 1 side and, non-sequential IPs on the other… i.e. If I have 10.10.10.4, 10.10.10.7 and 10.10.10.101 and those are the only addresses I want to put in the tunnel, Meraki can’t do it. With Meraki 0 it assumes a “branch office” is one big happy family, so everything at Site A should see everything at Site B. With a Watchguard its a pita. With Cicso it’s somewhat easy if you know the language, and with SonicWall it’s a breeze. It would be great to see a comparison chart of Firewall/VPN appliances that can do that.
Meraki FWs have some serious limitations for sure. Another big feature missing is source NAT. If you have duplication networks on both sides of the tunnel you have to find a different solution to make it work.
Gotta get some other UTMs in there to give Untangle something to compete against…since it’s the only UTM in the mix. Kinda like a multi-ton bank vault (Untangle) being compared against a screen door (pfsense) and a couple of wooden gates on a white picket fence! (the UBNT routers). We’ve done a lot of all 3…well, not so much PFSense anymore…used to do a bit of that, but it’s either Untangle (for most biz clients)…or UBNT gateways for the basic networks with simple needs.
I see that OpenVPN Server is listed under the UDM Pro. I can’t seem to find any information online about how to configure this. Anyone have any insights?
OpenVPN is not officially supported with the UDM-Pro so I do not recommend using it.
I’d be interested in a follow up for the UDM-Pro device as I think it’s way off the mark when you compare to pfsense or Untangle.
From a single pane of glass aspect the UDM-Pro fits, but re functionality pfsense and Untangle do things better.
I’ll be offloading my UDM-Pro ASAP and returning to pfsense or trying untangle, Sophos XG Home.
UXG-Pro “when” it arrives could be of more interest.