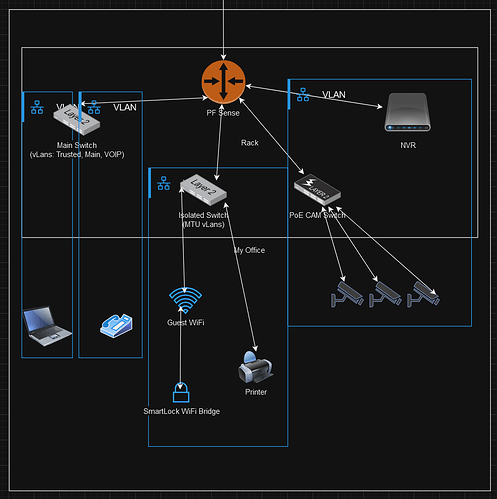
I am a freelance software engineer by trade and have never done any proper network management. I have never even used vLANs until recently. I have an small office for my freelancing business that I recently designed a network for and would be interested in any feedback from anyone who actually knows what they’re doing.
I have a Netgate SG-2100 PF Sense router, it has 1 WAN and 4 LAN ports.
The building my office is in takes in a fiber line and converts it to Cat6 in the basement somewhere and sends that up to my office, that plugs into my WAN port.
My Router, switches, and NVR are located in a small locked network cabinet.
My 4 LAN ports would connect to:
1: 16-port TP Link “Smart” switch which will handle 3 different tagged vLANs: (Trusted, Main, and VOIP)
Trusted and Main have free range to talk to each other, the main difference will be Trusted is connected to 1 specific Ethernet port that I connect my laptop into and that vLAN will be allowed to reach into other vLANs for config/management purposes.
2: 8-port TP Link “Smart” switch configured for MTU vLANs so each port is isolated and can only send packets to the uplink port which goes to PF Sense. This is my “Isolated” vLAN and will have the wireless router for my Guest WiFi Network (which will also isolate wifi clients so they cannot talk to eachother). I have a smart lock Wifi hub which will connect to that. I will also have my office printer wired up to the switch as part of my Isolated network (and PF Sense will allow both Trusted and Main vLANs to connect to the printer)
3: PoE Switch for security cameras
4: NVR for security cameras
(PF Sense will have LAN ports 3 and 4 sharing their own vLAN)
For IP addresses I plan to use: 192.168.(vlan tag).xxx
I have the following vlan tags planned:
Trusted: 10
Main: 20
Voip: 30
Isolated: 50
Cam: 90
Does this make sense. Is there anything I am missing or should consider changing?
At some point I want to also do something similar at home then setup a Site-to-Site VPN between my home and office networks. (Both are on gigabit fiber connections with the same ISP) Then I could have cameras and an NVR at home too and have all cameras across both locations record to both NVRs so even if someone steals the actual NVR or it gets destroyed in a fire or something that locations cameras will still have recordings I can access at the other locations NVR.