I wanted to compare performance of VPN options (OpenVPN / WireGuard) on pfSense 2.5.2 using an iPhone8 client utilizing a VZW cellular network. I wanted to mimic a similar situation where a remote client is attempting to tunnel back home using a VPN option in a typical “Roadwarrior Setup”. VPN options configured on a pfSense installation were both OpenVPN and Wireguard. Motivation for this experiment was based upon a random reddit post that suggested similar findings but without posting any configurations or setup details.
Configuration of Servers
pfSense OpenVPN Configuration
OpenVPN was configured with a hardened setup to utilize TLS1.3 (both iOS and pfSense 2.5.2 support TLS1.3, TLS 1.3 is not supported on pfSense versions < 2.5.0)
RSA-SHA256 CA and client Certificates Generated
Server Mode Remote Access (SSL/TLS + User Auth) Using Local Database
Protocol UDP on IPv4 only
Device mode tun
Port 1194
TLS Key Used which was 2048 bit OpenVPN static key shared between server and client
TLS Key Usage Mode TLS Encryption and Authentication
TLS keydir Use default direction
Peer CA Authority - CA certificate RSA-SHA256
Server certificate - Server Cert RSA-SHA256
DH Parameter Length 2048
ECDH Curve Use Default
Enable Data Encryption Negotiation
Data Encryption Algorithms AES-256-GCM AES-192-GCM AES-128-GCM CHACHA20-POLY1305
Fallback Data Encryption Algorithm AES-256-GCM (256 bit key, 128 bit block)
Auth Digest Algorithm SHA512
No Hardware Crypto Acceleration
Certificate Depth One (Client+Server)
Compression Disabled
DNS Default Domain Provided with Local DNS Server
Advanced Configuration
Custom Options (In order to enable TLS 1.3)
remote-cert-tls client
tls-version-min 1.2
tls-version-max 1.3 or-highest # use the highest available version if 1.3 isn't available
# TLS 1.3 encryption settings
tls-ciphersuites TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
# TLS 1.2 encryption settings
tls-cipher TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
reneg-sec 0
Send/Receive Buffer Default
Gateway creation IPv4 only
pfSense WireGuard Tunnel Configuration
Listen Port 51820
Interface Keys Generated
Firewall Rules WireGuard Interface Group
Interface Addresses 10.6.210.1/24
OpenVPN Client Configurations
OpenVPN Client Configurations were generated through pfSense Client Export Package utilizing the following settings within pfSense
Remote Access Server Server UDP4:1194
Hostname Resolution Other, Hostname openvpn.domain.com
Block Outside DNS - Checked
Use Random Local Port - Checked
Additional configuration options:
tls-version-min 1.2
tls-version-max 1.3 or-highest # use the highest available version if 1.3 isn't available
# TLS 1.3 encryption settings
tls-ciphersuites TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
# TLS 1.2 encryption settings
tls-cipher TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
OpenVPN client certificate created with designation of User Certificate, cn= RSA-SHA256
An example of the client configuration that was exported is the following:
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-192-GCM:AES-128-GCM:CHACHA20-POLY1305
data-ciphers-fallback AES-256-GCM
auth SHA512
tls-client
client
resolv-retry infinite
remote openvpn.domain.com 1194 udp4
setenv opt block-outside-dns
lport 0
verify-x509-name "domain.com" name
auth-user-pass
remote-cert-tls server
explicit-exit-notify
tls-version-min 1.2
tls-version-max 1.3 or-highest # use the highest available version if 1.3 isn't available
# TLS 1.3 encryption settings
tls-ciphersuites TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
# TLS 1.2 encryption settings
tls-cipher TLS-ECDHE-ECDSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256:TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256
<ca>
-----BEGIN CERTIFICATE-----
CA Cert Here
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
Client Cert Here
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
Client Private Key Here
-----END PRIVATE KEY-----
</key>
<tls-crypt>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
Static Key Here
-----END OpenVPN Static key V1-----
</tls-crypt>
The actual OpenVPN app on the Iphone8 (available through app store) was configured with following settings:
VPN Protocol Adaptive
IPV4-Only Tunnel
Connection Timeout 30 sec
Allow Compression No
AES-CBC Cipher Algorithm (unchecked)
Minimum TLS Version 1.3
Layer 2 Reachability (Checked)
Wireguard Peer Setup on pfSense
Enable Peer
Tunnel tun_wg0
Dynamic Endpoint - Checked
Keep Alive 25
Public Key (provided via iphone8 setup)
Pre-shared Key (Generated)
Allowed IPs 10.6.210.3/32
Firewall and NAT setup on pfSense
Firewall → Aliases → IP
Wireguard_Networks 10.6.210.1/24
Firewall → Rules → WireGuard
Protocol Ipv4* Source Wireguard_Networks Port * Destination * Port * Gateway *
Firewall → NAT → Outbound
Source Wireguard_Networks Source Port * Destination * Destination Port * NAT Address WAN Address Nat Port *
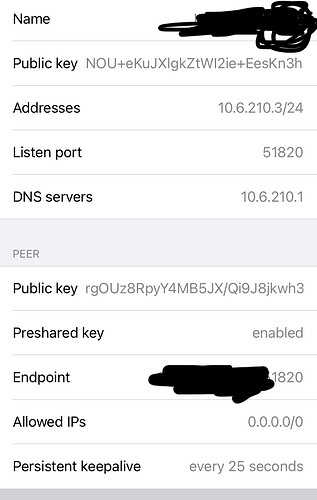
iphone8 WireGuard Peer Setup (Wireguard App Downloaded via App Store)
Private/Public iPhone8 keys generated via:
wg genkey | tee iPhone8.privkey | wg pubkey > iPhone8.pubkey
[Interface]
PrivateKey = <iPhone8.privkey>
ListenPort = 51820
Address = 10.6.210.3/24
DNS = 10.6.210.1
[Peer]
PublicKey = <pfSense iPhone8 peer public key>
PresharedKey = <psk as generated on pfSense>
AllowedIPs = 0.0.0.0/0
Endpoint = openvpn.domain.com:51820
PersistentKeepalive = 25
A lot of setup and configuation information, however hopefully that is enough information for anyone wanting to duplicate these tests.
RESULTS
SpeedTests were performed using Speedtest by Okla @ https://www.speedtest.net/
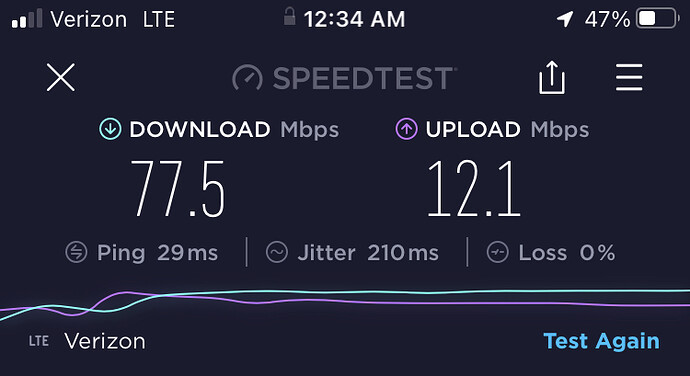
- Baseline Speed Test was peformed with iPhone8 on Verizon Network
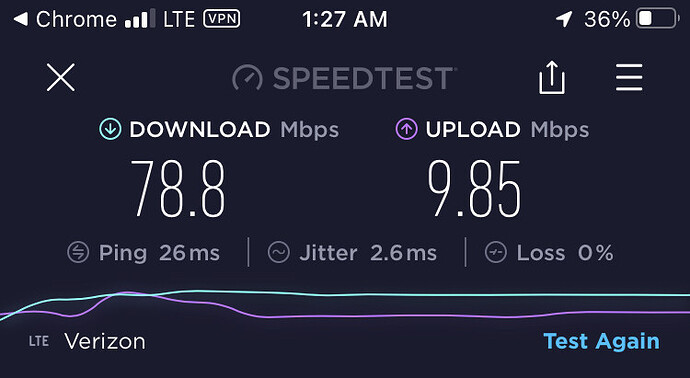
- Speed Test performed with iPhone8 (LTE connection) - tunneled through home pfSense server using OpenVPN via OpenVPN App from AppStore
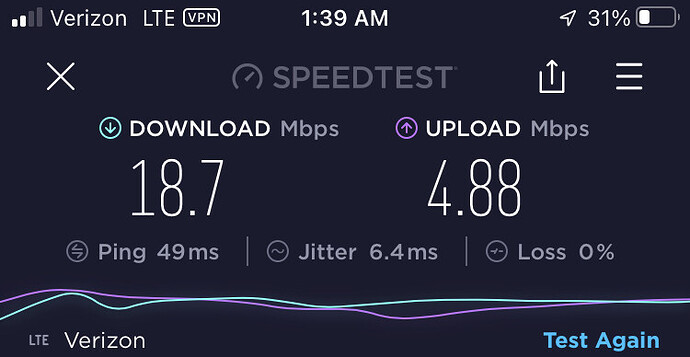
- Speed Test performed with iPhone8 (LTE connection) - tunneled through home pfSenser server using Wireguard via Wireguard AppStore Client
So In Summary for RoadWarrier Configuration Speedtest
Control:
iphone8 over Verizon LTE -
Download 77.5 Mbps, Upload 12.1 Mbps
Test Case #1:
iphone8 tunneled via OpenVPN / Verizon LTE through home pfSense -
Download 78.8 Mbps, Upload 9.85 Mbps
Test Case #2:
iphone8 tunneled via WireGuard / Verizon LTE through home pfsense -
Download 18.7 Mbps, Upload 4.88 Mbps
Perhaps I’m not testing what I think I’m testing with my Setup, however these numbers are fairly consistent over multiple tests with the OpenVPN setup roughly equivalent to Control and Wireguard markedly worse than control. I want to conclude for a road warrior setup, that OpenVPN is much better compared to WG, however I’m wondering if others are finding similar results.