I have a feeling this is going to be a stupid question. I recently had to do a clean install of pfsense, using Lawrence’s last pfsense install video. When I tried to put Quad9 as the DNS server, I couldn’t connect to anything. I used Cloudflare instead and it worked — somewhat. I’m still having some things not resolving and I’m getting erros that say Cloudflare can’t resolve. I’m thinking I screwed up a setting somewhere, but I can’t figure out what. After two days of research, I’m still not finding anything. The install is dead simple. I’m not even sure if a lot of the problem isn’t on my PC, rather than the router. Can anyone tell me why Cloudflare would work and why Quad9 wouldn’t?
Where did you specify the DNS change? Did you do this on DHCP or did you apply this to the router itself under the general settings?
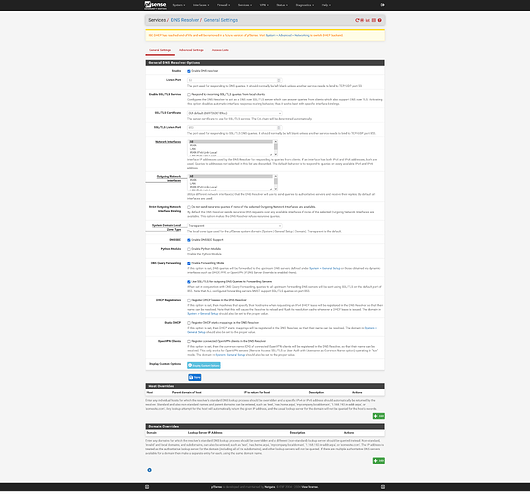
What does you DNS resolver settings look like? Screenshots would help.
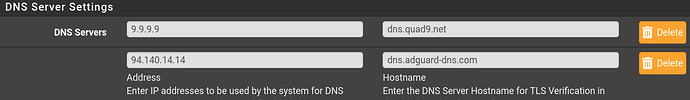
System > General Setup, add 9.9.9.9, Save

nslookup 9.9.9.9
9.9.9.9.in-addr.arpa name = dns9.quad9.net.
Maybe try this for the DNS settings. I’ve had some trouble with CloudFlare not resolving some local government sites.
And these settings in Services > DNS Resolver > General
Okay, thank you all for the responses. Quad9 seems to be working now… Should I have more than one DNS server listed?
@xMAXIMUSx: I did it under general settings. As for screenshots of the DNS resolver, that would be a big image. Would a piece of it be useful? I’m happy to provide whatever screenshots would be helpful, but I’m not knowledgeable enough to know what would be helpful.
@ryan_g: I’m trying the settings you’ve suggested. We’ll see how it goes.
I still think there’s something hinky with my network, but I can’t point to anything, other than wi-fi working sometimes and not others.
Incidentally, I checked the logs and didn’t see anything worrying there.
I didn’t think DNS works as a failover, that is if you have 3 servers pfsense uses the fastest server …
Thanks, good to know.
This worked for Quad9. Thanks.
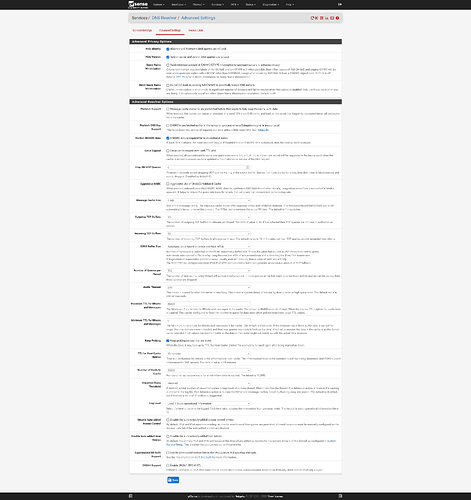
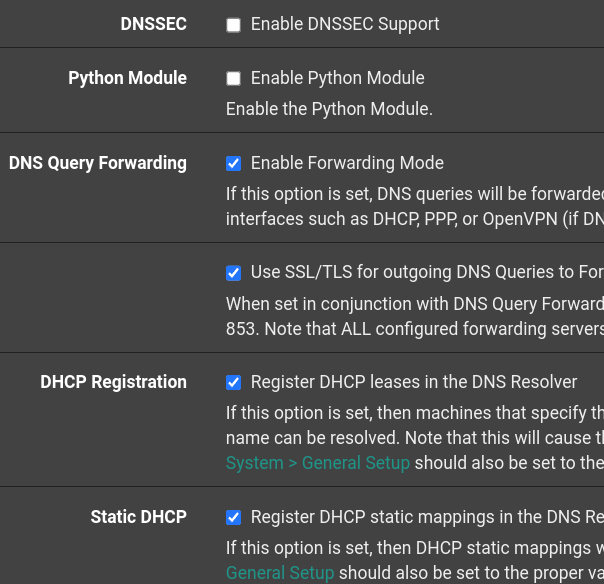
I apologize, I was looking at the wrong page. Here are the screenshots for the DNS Resolver settings.
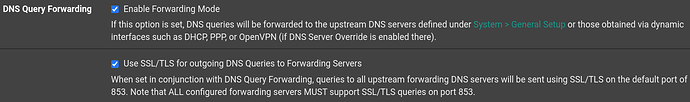
I don’t think you want DNSSEC on as ‘Use SSL/TLS’ handles the encryption for DNS forwarding. The DHCP registrations are on if you have static IPs set. I use the Host Overrides in conjunction with that for internal servers. That way it resolves to local IP addresses when using the FQDN.
I changed the setting. I then reset my switch, rebooted my computer and restarted my router. Strangely enough, and I’m not saying this is related, I’m getting an Internet connection ---- for about ten minutes before it stops. Then I have to reboot my computer. Also, my NAS, et al, aren’t pulling an Internet connection, either. This is weird. Some stuff is getting through, but not other stuff.
Seems odd that it quits working after a couple minutes. Hardware failure maybe? Is the Unbound service crashing? You could try using the Service_Watchdog package to restart it automatically but there must be something else going on.
Just trying to help, maybe someone else has a better answer ![]()
While DNS over TLS and DNSSEC are both security features, they are designed to protect very different things.
DNSSEC is designed to protect applications that use DNS from accepting forged or spoofed DNS data. All responses from DNSSEC-protected zones are digitally signed, allowing a DNS resolver such as Unbound (if the DNSSEC checkbox is enabled) to verify that the information is identical to the information published by the zone owner and served on an authoritative DNS server.
DNS over TLS, on the other hand, adds transport layer encryption that encrypts the DNS queries you send to and the responses you receive from a DNS resolver, similar to how HTTPS encrypts traffic sent to and from an HTTP server.
So while you’re right that enabling DNS over TLS is the most useful thing to do in this particular case, it’s not an either/or question, because even with Unbound running in forward mode, sending the queries to an upstream DNS resolver over an encrypted connection, it may still make sense to enable DNSSEC as well, since it can still validate the DNS responses it receives from the upstream resolver, which in this case is Quad9.
Of course, if you trust Quad9 not to tamper with any responses before sending them back to you, you may as well leave it disabled.
Disable DNSEC and only enable ‘DNS Query Forwarding’ and ‘Use SSL/TLS for outgoing DNS queries to Forwarding Servers’ this should solve the issue.