Tom, I need some clarification regarding DNS when using VPN.
I am running an OpenVPN client routing ALL traffic (well except the Apple TV) though a VPN Tunnel on my pfSense Box.
pfSense is set to use 9.9.9.9 as DNS and override not allowed.
Q1: This means that all DHCP clients, not overriding DNS will use 9.9.9.9 - and access it through the tunnel - invisible to the ISP ?
Q2: If a client overrides DNS - going to say my ISP DNS - the request will still go through the tunnel and be anonymous ?
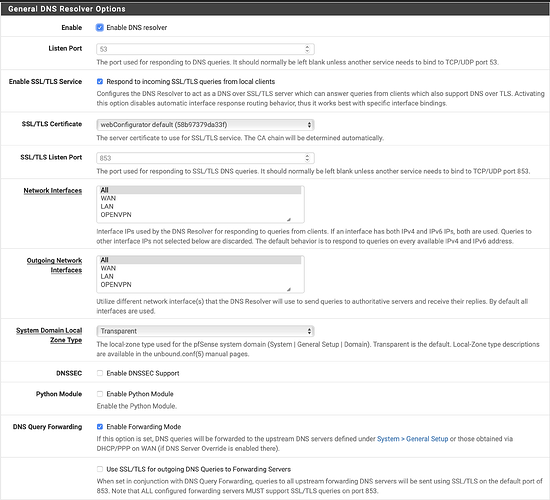
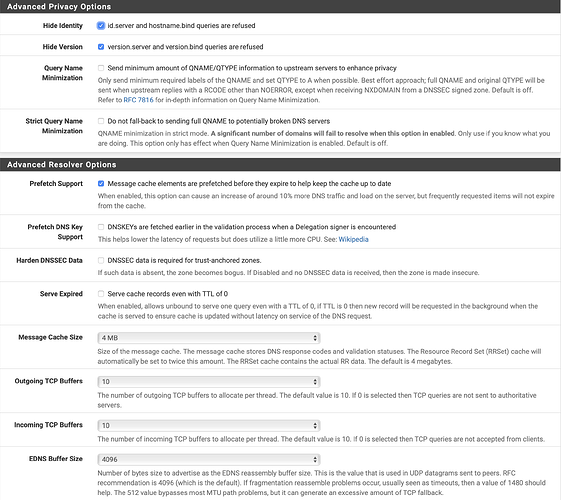
I have enabled DNS over SSL using these options:
server:
forward-zone:
name: “.”
forward-ssl-upstream: yes
forward-addr: 9.9.9.9@853
forward-addr: 149.112.112.112@853
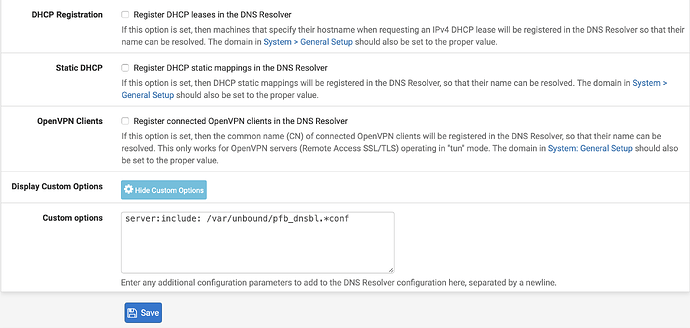
server:include: /var/unbound/pfb_dnsbl.*conf
That should further hide DNS for even the VPN Provider ?
As long as you have ALL traffic going through the VPN the DNS traffic should be too,
Who is your VPN provider ? If the DNS is resolved outside the vpn tunnel I’m pretty sure that is a DNS leak. You should test it. https://www.dnsleaktest.com
I’m on AirVPN I’m using their DNS server, as I connect via an IP address there is little chance of a DNS leak.
Personally it doesn’t make sense to use DoT if you have a VPN, just use the VPN. I’ve now switched over all my traffic via VPN but I still have issues with gmail / payment sites / financial sites when I go via my ISP. Though it’s probably more effort for the ISP to snoop on you if you don’t use their DNS or encrypt DNS though I doubt much more.
At least in the UK I haven’t come across any news of the ISPs up to any nefarious activity though it doesn’t mean they aren’t up to something.
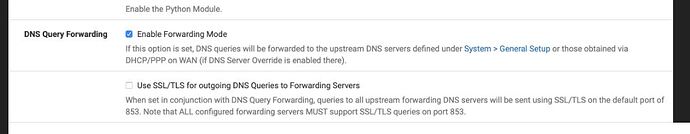
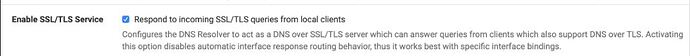
I can’t resolve any queries when I activate “Use SSL/TLS for outgoing DNS Queries to Forwarding Servers”
When I try to lookup www.apple.com with activated TLS I get “www.apple.com -> The operation couldn’t be completed. (kCFErrorDomainCFNetwork error 2.)” from my Macbook.
All works fine when I disable TLS.
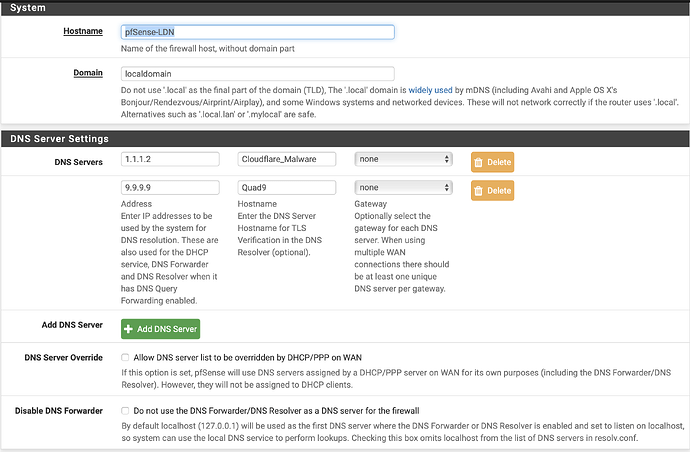
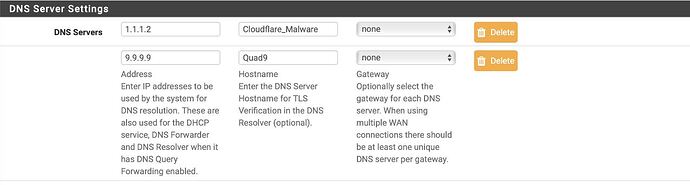
I use 1.1.1.2 and 9.9.9.9 as DNS Servers.
Can someone help?
Try going through the step in my video again and check the logs in pfsense.
Make sure that you ISP’s modem does not have the same DNS settings as you pfSense system. For example, my ISP’s modem DNS setting are Cloudflare addresses whereas my pfSense DNS settings are Quad9 addresses.
If problems persist, then put up screenshots of you pfSense settings.
Ive changed the ISPs modem DNS to 1.1.1.1 and 149.112.112.112.
The pfSense DNS is set to 1.1.1.2 and 9.9.9.9
From what exactly do you need a screenshot?
Okay…make your ISP modem’s DNS settings from one provider and the DNS settings for your pfSense system from another DNS provider. What you did…in your DNS settings…
Now, send screenshots of:
System / General Setup
Services / DNS Resolver / General Settings
Services / DNS Resolver / Advanced Settings
I have changed my ISP Modem DNS to 9.9.9.9 and 149.112.112.112 -> Quad 9 and the pfSense to 1.1.1.2 and 1.1.1.1 -> Cloudflare.
Still the same result, I can’t resolve any domain on my MacBook with TLS enabled.
I have done that but its still not working when I turn on SSL/TLS for outgoing DNS Queries.
When I dig www.apple.com I get the following error:
dig www.apple.com
; <<>> DiG 9.10.6 <<>> www.apple.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 33144
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.apple.com. IN A
;; Query time: 43 msec
;; SERVER: 192.168.10.1#53(192.168.10.1)
;; WHEN: Thu May 28 23:50:49 CEST 2020
;; MSG SIZE rcvd: 42
I saw in the DNS Resolver log an error:
error: ssl handshake failed crypto error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
and
notice: ssl handshake failed 1.1.1.2 port 853
What Cert does it mean?
1.1.1.2 is cloudflare. Did you try just 1.1.1.1?
yes and I still get the same error:
notice: ssl handshake failed 1.1.1.1 port 853
unbound 41892:2 error: ssl handshake failed crypto error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
I took the names out and it works now!
Thank you!