Hi! Just saw the video. Thanks for the review! I’m the Executive Director of Quad9. I’ve got a few answers and comments based on the video.
First: We’re a very small 501( c )3 non-profit, but we punch well above our weight in a lot of ways despite having only a fraction the capitalized size of any of the other services you put in the list. We’re always looking for sponsors, both individual and corporate - see our webpage for the big friendly “donate” button.
Second: We’re a really great security service, but we also aren’t selling personal data, nor do we have some hidden plan by giving away our service for free. We’re not upselling you to a paid plan, nor are we promoting our other hosting or DNS or marketing, nor are we selling or digesting your private data. In fact, we never even transmit your IP address out of the cluster of systems in each city where we receive it, nor do we ever write it to any sort of storage. Furthermore, we have no accounts, no signup, and no way of tracking who are users are - it’s entirely free, and we really don’t even want to know who are users are. The downside of that is that there isn’t any customization or reporting, because that would imply tracking information and storage. We’re explicitly designed not to be able to retain personal data from the ground up. This is actually a very appealing part of our project for schools, public networks, and of course everyone in the areas covered by GDPR regulations, and I think we’re the only service in the world operated by a non-profit with these goals.
To the person who references rumors that we are part of a vast government conspiracy: No. Our staff, and board, and sponsors are all working towards making Quad9 the most private service available. Specifically, everyone working here would depart if anything nefarious like that were the case, and I’m sorry that our reputations for privacy fanaticism can’t easily be represented in a clickable format. We find that some of our goals may align with certain law enforcement organizations who focus on financial crimes (stopping cyber-crime is fundamental to both of our missions) but that’s the only place where the Venn diagrams cross. We are currently funded only by private donations, mostly by cyber-security companies who value our work, individuals, and quite a bit of in-kind donations from other non-profits and service providers for network capacity.
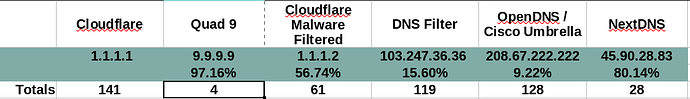
Third: Our security coverage is pretty great, and I’m pleased to see your numbers bear that out. The reason we’re so awesome is because of our threat intelligence partners. We don’t actually evaluate threats and figure out who is doing what - we ingest lists from around 19 different companies, and some open lists and then our job is to relay/apply that data via our DNS servers. This is very different than everyone else, who may be building the lists themselves, or who have only a limited number of providers. The companies that give us these lists of malicious/phishing/command&control/etc. hosts is because we give them some insights as to the volumes of “hits” happening on the domains they give us. We don’t tell them anything about your personal data (no IP addresses) but they find the volume data to be super-useful with our many millions of end users giving immediate validation to growing or falling trends in malicious domains. Also, you can find out who provided us with any domain that is blocked by going to our web page - there’s a search bar right on the front. We don’t have any “hidden” suppliers of threat data - everything is public about individual domains, though we don’t publish the list itself.
I suspect the SANS list is being ingested by one or more of our TI providers and analyzed for false positives, and then re-bundled and sent to us in part. We don’t (yet) take that list directly. This is actually quite common - finding false positives is a science all to itself, and we are extremely sensitive to FP entries. Many of the public lists are more prone to FP data, so we constantly are looking for issues in the data and working with both open and closed list providers to keep false positives low or nonexistent.
Fourth: We’re in more than 150 cities and 90 countries now, and still growing, so there’s probably a server close to you, and you get routed there automatically. Anycast is fantastic.
Fifth: We support DNS-over-TLS, DNS-over-HTTPS, and DNSCrypt protocols for extra interception-proofing. The newest Chrome being rolled out & Android =>Pie will auto-upgrade to encrypt DNS connections to Quad9, and the very early beta versions of Windows as well. Encryption is good!
Sixth: We have multiple “flavors” of the service. There is 9.9.9.10, which provides “vanilla” DNS with no blocklist similar to CF and Google’s service, and in fact there is even no DNSSEC on that address to make it even more able to resolve everything, even things it shouldn’t (user beware!) There’s also 9.9.9.11, which has blocking + ECS, which is a whole different story but the summary is that some CDNs will work better to get you to the closest server at the cost of some privacy leakage (the ECS protocol sends some parts of your IP address to the remote DNS server during the lookup.) Also, we try to encourage everyone to set up their “secondary” server as well as the backups to minimize effects of routing issues or maintenance windows.
9.9.9.9
149.112.112.112
2620:fe::fe
Thanks again for the review - I’ll try to keep my eye on this thread to answer any questions.