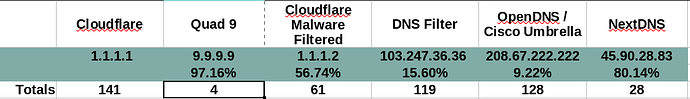
There were quite a few YouTube comments asking about NextDNS. I setup an account and then I ran the query against their services. While they did better than DNS Filter, Umbrella, and Cloudflare Filtered, Quad9 is still by far the winner in this test.
4 Likes