OK, so today I took the time to convert the switch back to Layer2.
- I have shut down the Unify devices
- Cleared the DHCP leases in pfSense firewall
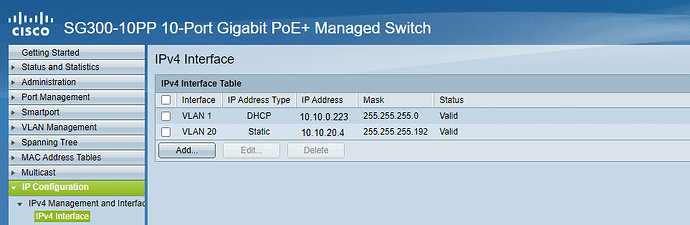
- Performed a factory reset on the SG300 and left it in L2 mode.
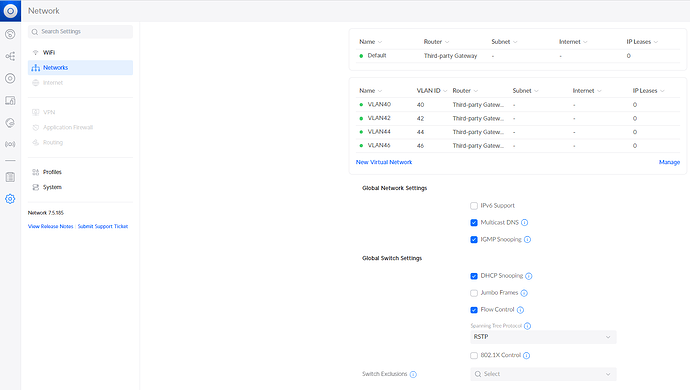
- Configured all VLAN in the switch and assigned the corresponding ports to it:
* Configured ports 9-10 as a LAG port. (same for pfSense)
* Port 1-3 has VLAN 20 as “untagged” and VLAN 40,42, 44 and 46 as “tagged”
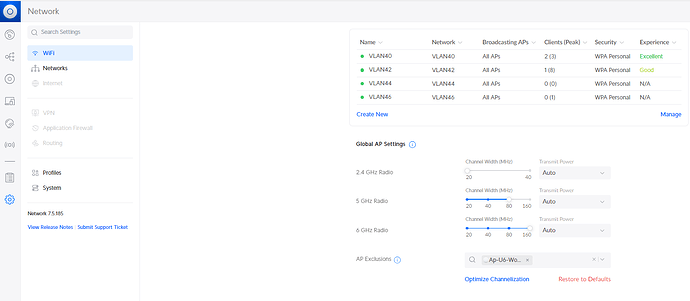
But when I connect to the different Wi-Fi networks, I still get only IP addresses assigned to the VLAN 40 network.
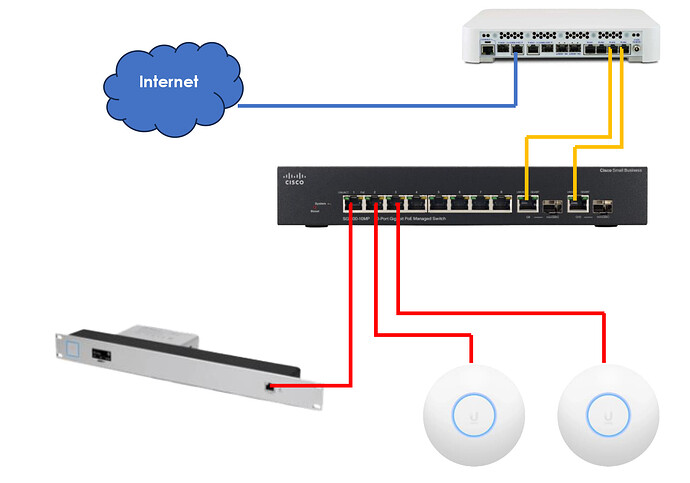
Still confused in where the problem might be, in the pfSense device (Netgate SG6100), the switch (SG300-10PP PoE+ which now is configured as a L2 switch) or my Unify setup. (CloudKey G2 Plus with two U6 access points)
Below is the new config of the Cisco switch:
KSG300-10PP#show running-config
config-file-header
SG300-10PP
v1.4.11.5 / R800_NIK_1_4_220_026
CLI v1.0
set system mode switch
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
vlan database
vlan 10,20,30,40,42,44,46,50,90
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
hostname SG300-10PP
username stefan password encrypted 2e8b782741518a1c5e29430ee6eabb38d99c3616 privilege 15
ip ssh server
snmp-server location ""
snmp-server contact
!
interface vlan 10
name DMZ
!
interface vlan 20
name Management
!
interface vlan 30
name Servers
!
interface vlan 40
name vlan40
!
interface vlan 42
name vlan42
!
interface vlan 44
name vlan44
!
interface vlan 46
name vlan46
!
interface vlan 50
name "VPN Users"
!
interface vlan 90
name "Virtual Servers"
!
interface gigabitethernet1
description UCK-G2-PLUS
switchport trunk allowed vlan add 40,42,44,46
switchport trunk native vlan 20
!
interface gigabitethernet2
description AP-U6-#1
switchport trunk allowed vlan add 40,42,44,46
switchport trunk native vlan 20
!
interface gigabitethernet3
description AP-U6-#2
switchport trunk allowed vlan add 40,42,44,46
switchport trunk native vlan 20
!
interface gigabitethernet6
switchport trunk allowed vlan add 10,20,30,40,42,44,46,50,90
!
interface gigabitethernet7
channel-group 2 mode on
!
interface gigabitethernet8
channel-group 2 mode on
!
interface gigabitethernet9
channel-group 1 mode on
!
interface gigabitethernet10
channel-group 1 mode on
!
interface Port-channel1
description "TrunkLink pfSense"
switchport trunk allowed vlan add 10,20,30,40,42,44,46,50,90
!
interface Port-channel2
description "TrunkLink Cisco"
switchport trunk allowed vlan add 10,20,30,40,42,44,46,50,90
!
exit
banner login ^C
SG300-10PP 10-Port Gigabit PoE+ Managed Switch
^C
SG300-10PP#exit