Putting this under networking as it feels like a DNS related issue.
I am trying to install certificates on my synology server without having to poke a hole in my firewall to do so. The advertised method seems to be opening up the synology to the external internet, then creating a certificate through the GUI.
pfsense is the internal DNS resolver so that the synology server has a DNS name and IP. And the domain for the subnet (mydomain.org) is maintained externally.
So I used certbot to generate certificates that are signed by letsencrypt and validated through manual DNS. Getting certs is not a problem. I end up with key, crt, fullchain and chain files. They import smoothly in the the Synology server.
I am not sure I am using the correct domain though to setup the certificates. Right now I specified a wildcard domain. For example “*.mydomain.org”. The internal domain entry for the synology is “smaug.mydomain.org”. I assumed the cert would cover it. I also tried smaug.mydomain.org, mydomain.org and the combination of all three.
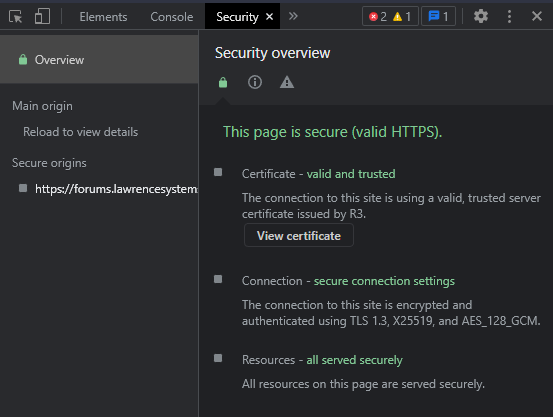
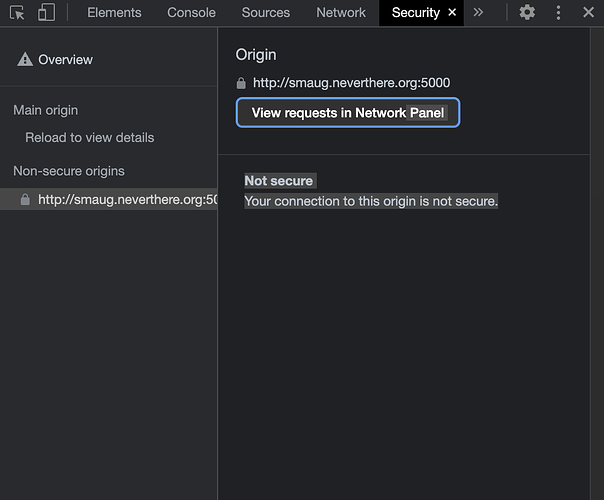
When I install the certificate and the Synology webserver is restarted the browser shows the connection is still insecure.
What step or fundamental concept am I missing?
Michael