Hey, we are a 100% Azure house.
Azure does have a lot of very expensive options the most expensive is the Microsoft Azure Premium Firewall Crazy right!? NO, I know it is expected. What is CRAZY is that really expensive firewall only has one IDPS rule set and does not have any signature rules related to https traffic it only detects IDPS malicious traffic if it is HTTP so the traffic as to be decrypted to get detected, even though we have TLS inspection enabled, Crazy right? Created a ticket with Microsoft they said Yeah it will not detect any IDPS if it is Encrypted traffic!
So Looking to replace it.
We are looking for a standard Stateful Firewall that can do deep TLS inspection has flexible and or customizable rule sets for IDPS and decent threat intelligence functionality.
It needs to be billed through Azure so it would have to come through the market place.
there is only one Open Source option.
basic OPNSense… Does not say NGFW but has features.
The others are
VT AIR Next Generation Enterprise Firewall
Versa SDWAN & NGFW for Azure Virtual WAN
Forcepoint Next Generation Firewall
Fortinet FortiGate Next-Generation Firewall
VM-Series Next-Generation Firewall from Palo Alto Networks
Was all set to go with Fortinet (not as expensive and name recognition), but I saw Tom’s review and looked at the CVE associated with them, and now I am rethinking.
I tried to look at the the CVEs for each and they all are similar and it hard to compare.
Is there a neutral 3rd party that evaluates firewalls?
Do you have any advise/experience with these Products can you give me any advice?
Regards
Mo
I use Palos and they are one of the best on the market IMO. You can check Gartner or Cyberratings.org. I can appreciate that Fortinet wouldn’t be a popular choice, but I would check the CVE to see if it affects a feature you would be using.
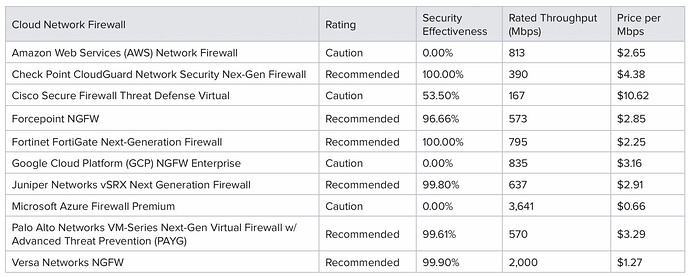
Either way, here is a nice chart to get you started. CyberRatings.org Publishes Test Results on Cloud Network Firewalls - CyberRatings
OPNsense is not NGFW, you can gain some of those features through ZenArmor but you are going to need to buy that to get close to what you want.
You might be able to use Zenarmor alone, you’d need to check on that. I’m not an Azure person so I don’t really know what you can put in front of your traffic.
Unless you are putting in certificates to allow for the firewall decrypt the traffic IDS systems are not too useful for encrypted traffic. They just fall back to doing IP blocking. If you are looking for good IP blocking then you can take a look at https://www.crowdsec.net/
My recommendation is Palo. That’s our main datacenter/cloud firewall at work (Fortune 500) as both physical appliances and Azure VMs. The features are there and stable and you’ll find good documentation and have a lot of expert options to help you.
Managing Versa SDWAN/NGFW is my actual dayjob (we use it for the SDWAN but also use the NGFW features at the branch level), it has the features you’re looking for but you can’t just run one system and manage it directly, it needs a minimum 6-node cluster to manage it (Director, Controller, Analytics, two of each) and you will not be able to self-learn it unless you make it your full time job for 6 months before putting it in production. Maybe two months with paid training courses or paying for professional services. And there are some consultants you can hire but much fewer than others. Also, its an SDWAN product foremost with a good NGFW added on, they aren’t trying to compete in the NGFW-only market.