Before getting to my problem, I wanted to do a summary of my system.
My Unifi network consists of:
- 16 port and 8 port POE layer2 switch
- (3) AP-AC-PRO’s
- 24 port layer2 switch
- USG3P router (considering Netgate with Pfsense if it can help)
I have 4 VLANs (LAN, Iot, Camera and Guest). Camera and Guest are working great (thanks Tom for the videos) so this is limited to the LAN and IotVLAN.
My devices are:
- Roku Ultra (hardwired on IotVLAN)
- Sonos player\speakers (hardwired on IotVLAN)
- Phones and tablets that need to connect to Sonos and Roku (Wireless on IotVLAN)
- Alexa Echo dots (Wireless on IotVLAN)
- Synology NAS for storing personal files and media for DLNA server (hardwired on VLAN1)
- Notebooks and automation PC (hardwired on VLAN1)
After reading multiple posts and searches, the suggestion was to place all high risk devices in a separate IotVLAN while keeping the low risk devices in a management VLAN1. So that is what I did. Where I started running into problems is the when the VLAN1 devices (items 1-4) need to connect or provide services like DLNA across the two VLANs. As far as I can determine is the problem is with the broadcast data being blocked. This is no surprise sense VLANS are made to provide isolation but to get around this, you have to look for work arounds.
I have done the normal things like:
• Turned on mDNS
• Enable IGMP snooping
• Turned on UPnP (yuk)
• Enabled igmp-proxy through a JSON file.
• Through firewall rules, opened up the ports that Roku, DLNA and Sonos uses
Still, after all this, still cannot get the DLNA to work.
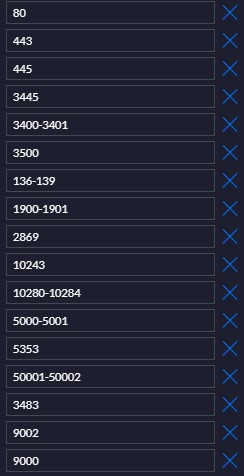
I know there are posts out there with people having limited success but still make me ask the question, “Are IOT VLANS incompatible for Home media devices?” or am I missing something.
Would Pfsense be better at allowing media devices across VLANs?