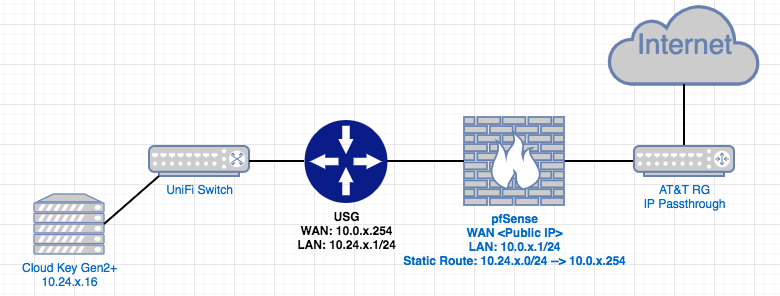
I’ve been trying to get a USG setup properly behind a Netgate SG-3100. The goal being to get DPI and the rest of the dashboard in UniFi controller functioning. Following the Guide to disabling NAT on USG at the ubnt forum, I disabled NAT via a shell script on the USG, not a JSON file where the controller resides. My problem is I’m not getting any traffic coming through the USG WAN port which I’ve connected to a LAN switchport on my Netgate.
Here’s the script I used. The line where I retrieve the date/time is a another way for me to verify the script executed.
#!bin/bash
cmdwrap=/opt/vyatta/sbin/vyatta-cfg-cmd-wrapper
$cmdwrap begin
Disable NAT
$cmdwrap set service nat rule 5999 exclude
$cmdwrap set service nat rule 5999 outbound-interface eth0
$cmdwrap set service nat rule 5999 type masquerade
echo $(date) >> /home/atlas61/runtimes
End changes
$cmdwrap commit
$cmdwrap end
Here’s my setup:
On the USG side:
- I uploaded my script to USG directory /config/scripts/post-config.d
- Made it executable using chmod +x [filename]
- Setup port forwarding so that everything entering WAN goes to LAN interface
- LAN interface is 10.24.x.2
- Enabled DHCP on LAN interface 10.24.x.100 - .200
On the Netgate side:
- Setup a gateway to USG WAN 10.0.x.254
- Setup static route to 10.24.x.0/24 through USG WAN 10.0.x.254
- Setup rule on LAN1 interface so that anything coming from 10.24.x.0/24 is passed.
- Disabled DHCP for LAN1 interface.
USG was rebooted and I verified NAT was disabled using ‘show nat rules’
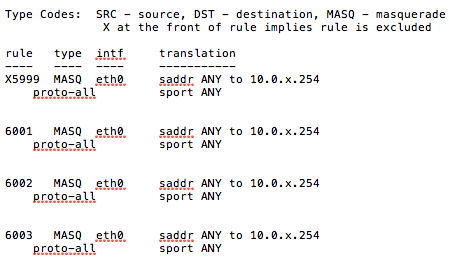
Do I need additional rules on the Netgate side to get this working? The USG?
Your input is appreciated. Thank you.