Hi Tom and Forum crew
I’ve been watching a lot of Tom’s videos regarding VLANs on Unifi/PFsense and have bought a bunch of Unifi hardware to work on.
I have all the config working as expected until I assign a VLAN to an SSID as which point I cannot connect to the SSID because my device cannot resolve it’s DHCP on that SSID. I’ve tried both VLAN only and Corporate VLAN with DHCP pool configured and neither seems to work. I’m guessing I need to allow traffic to the WLAN somehow but I can’t find the right combination.
For information more than anything, I’m using a USG Pro4 With a managed POE switch on LAN1 and a Nano HD for WiFi. I want to scale this to multiple WLANs across multiple WAPs, but at the moment I can’t get the basics to run properly.
VLAN only means to set up the VLAN on the switches, and not on the router. Corporate VLAN (and Guest VLAN) mean to set up the VLAN on both the switches and the USG.
Make sure the switch ports that the USG and nanoHD are plugged into both have the “All” profile - this means to automatically include all VLANs which are created. Also make sure that the switch ports don’t have any profile overrides. If you want to use a custom profile, then make sure that the VLAN you made is selected as “tagged” in that profile.
I assumed about that your POE switch is a Unifi switch, since you said its an “All Unifi backbone”. If it isn’t a Unifi switch, you’ll need to create the VLAN manually on that switch, and make sure it is tagged on the necessary ports.
1 Like
Hi brwainer
Thanks for your reply. First up yes everything is unifi head end to WAP.
Sorry if any of the below is dumb, I’m just wrapping my head around this for the first time.
So the practical difference between VLAN only and Corporate VLAN is that corporate goes all the way through the setup from head end to WAP? I believe this is what I want as we are endeavouring to create a whole separate subnet for a company inside our building which is letting a small office from us. They need access to the outside world but not to our network (obviously) and I want to be able to maintain control of the switch and UAP.
Unless you can suggest a simpler way to configure this end result?
The trunk port that connects back to the USG have to have a specific profile “All” and the same for the USG trunk port. I presume that the VLAN traffic remains segregated due to the tags then?
And then I also assume I’m right that I need to then select a number of ports to assign to the VLAN network ports and to the UAP that will be sending out their own SSID?
Regards, David
To get internet access on a new SSID on a new VLAN, this should be all that is required:
-create a new network, Corporate or Guest type, and assign it a VLAN number and whatever subnet you want (should not overlap with any other network). This creates the VLAN, subnet, and DHCP server on the USG, and the VLAN on the switches
-create a new SSID and put in the same VLAN number
I am not sure what you mean by “ select a number of ports to assign to the VLAN network ports”. If you want some switch ports for wired devices to go to that VLAN only, then yes you would change their profile to that VLAN. For your APs you should always use either the “All” profile, or make sure that if you create a custom switch port profile that all the necessary VLANs are selected.
1 Like
It might be worth trying to untag a switch port on the VLAN for your new SSID and try hard wiring it in just to remove the wireless leg as a possible problem.
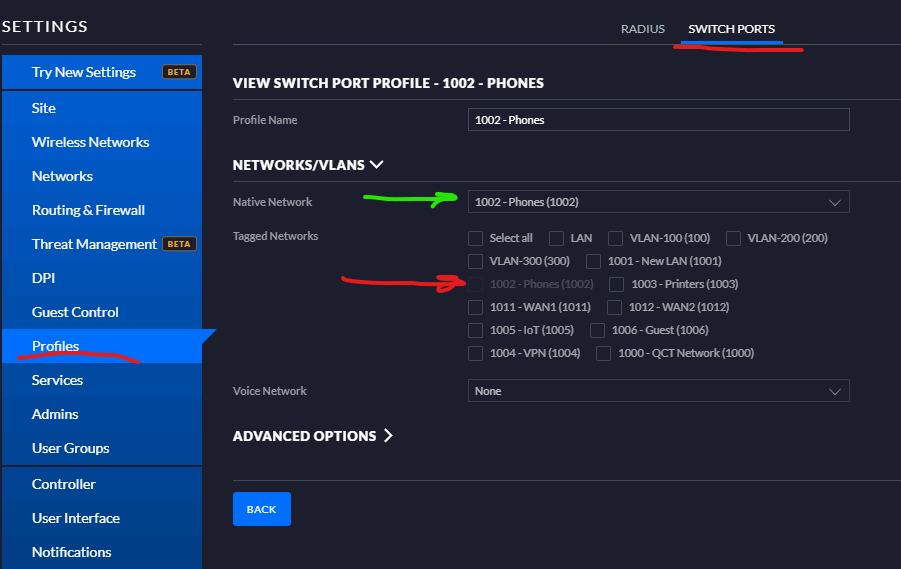
I’ve done quite a bit of playing around with my system so I don’t remember what the default is but I think in your controller you go to devices, click the switch select the ports tab, click the edit pencil on the port you want then change the switch port profile to the vlan you want. Apply the change at the bottom and give it a few seconds.
If you are unsure which profile is just untagged (no tagged vlans) then you can either click the “manage profiles” link under the switch port profile box or go to settings, profiles, switch ports tab, view. The example I’ve attached is tagged on no vlans (big red arrow), untagged (native network, big green arrow) on 1002.
Once you know that wired traffic is getting from the router to your switch and from your switch to your device then you can troubleshoot the wireless leg.
1 Like
Hi again,
Thanks to those that helped. I have now solved it.
I deleted and recreated the profiles (setting the LAN as the native network and tagging all neccesary VLANs for a given switch port) and got it working as intended.
Thanks for taking the time guys. Much appreciated, sorry for the slow post, it’s been hectic here.
Regards