Well they finally did it. TNSR is available for home lab. I’ve spun one up as a vm which given my gear might un do all the wonderful performance offered in their new binaries (VPP DPDK…)
First impressions. Setup.
Text based menuing, pretty straight forward. I opted to not configure interfaces during initial setup, so once installed I had to remove and interface from the tnsr overland process. This returns the hardware back to the vm os for configuration, for mgmt needs etc. Once tnsr owns a nic, it OWNS it. Which is nice as it does not bind ssh or other services to the interface which is a good security practice.
NAT. Easy enough, their zero to ping instructions are very easy and do a great job of getting you up and running quickly. Performance. I have symmetric gig, and tnsr and my pfsense and my usg all seem to do a good job of flodding the hell out of it, so I lack a pipe large enough to see if and where TNSR can pull away in simple nat.
So that is easy enough, but the main test I’m looking at is IPSEC performance for site to site.
USG caps at 90mbps and takes the cpu down inducing traffic failures for anyone else behind said usg. In my opinion this is totally a no go for the usg. If u need ipsec… keep trucking.
Pf sense. With concurrency enabled and throwing 6 cores at it I rock 500 to 600 mbps with the cpu only around 40%. This is very usable and doesnt take so many resources from the rest of the system so anyone else behind the pfsense will still have maintain good internet access.
TNSR. 1 day gone, tunnel will not form to my fortigate 3601E back on campus. Which sucks but I won’t give up. Ipsec on vpp should go full gig no problem (according to the glossies)
More to come!
Good to hear you got it up and running. I have not done any testing with it yet. 
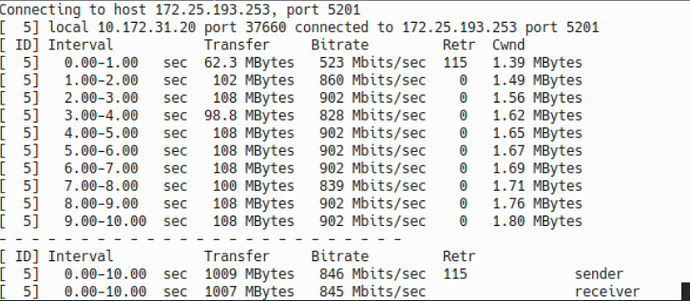
It works. And its faster, about double the speed on back to back tests.
Here is screenshot of iperf across teh IPsec Tunnel.
Here is teh output of IPSEC tunnel status query on the TNSR.
My issues on setup.
1: Zero to Ping instructions great but the ACL blocks the IPSEC tunnel setup traffic. (Me Derp)
2: Tunnel status query commands goes OTL when phase 2 is failing. Made “1” very dificult to diag as it appears teh tunnel just totally dies when I pulled the acls. That was a rabbit hole which required pcaps and wireshark to figure out.
3: Fortinet config required some tweaking and Replay Protection looks to be part of my initial problem.
Future. I have another 3601 I am going to peer in (so I should be able to figure out whats up with replay.
But otherwise… Man, the hype is not hype. From teh same VM host (a Socket 2011 6 core sandy bridge) Im getting double the throughput on the tnsr VM as the pfsense VM on the same box (with much more vm cores and ram thrown at it…). These tests use teh same bridged port off teh host going to the same port on the ISP router.
[admin@tnsr-home ~]$ /usr/bin/clixon_cli
Netgate TNSR Version: tnsr-v20.08-3
Expires on: Wed Feb 17 08:44:35 2021
For information see ‘show documentation’
tnsr-home tnsr# show ip
ip ipsec
tnsr-home tnsr# show ipsec tunnel 0 verbose
IPsec Tunnel: 0
IKE SA: ipip0 ID: 1 Version: IKEv2
Local: REDACTED[500] Remote: REDACTED[500]
Status: ESTABLISHED Up: 1302s Rekey: 4543s
Local ID: REDACTED Remote ID: REDACTED
Cipher: AES_CBC 128 MAC: HMAC_SHA1_96
PRF: PRF_HMAC_SHA1 DH: MODP_1024
SPI Init: 15882757486468878759 Resp: 17385364628153358636
Initiator: true
Child SA: child0 ID: 1
Status: INSTALLED Up: 1302s Rekey: 1928s Expire: 2299s
Received: 0 bytes, 0 packets
Transmitted: 0 bytes, 0 packets
Cipher: AES_CBC 128 MAC: HMAC_SHA1_96 PFS: MODP_1024%IKE
SPI in: 2174133907 out: 3777726983
IKE SA: ipip0 ID: 3 Version: IKEv2
Local: REDACTED[500] Remote: REDACTED[500]
Status: ESTABLISHED Up: 1299s Rekey: 4559s
Local ID: REDACTED Remote ID: REDACTED
Cipher: AES_CBC 128 MAC: HMAC_SHA1_96
PRF: PRF_HMAC_SHA1 DH: MODP_1024
SPI Init: 8084055267741315808 Resp: 16811901007837471734
Initiator: no
Child SA: child0 ID: 2
Status: INSTALLED Up: 1299s Rekey: 1587s Expire: 2301s
Received: 2768211688 bytes, 2211174 packets
Transmitted: 2256117340 bytes, 2211174 packets
Cipher: AES_CBC 128 MAC: HMAC_SHA1_96 PFS: MODP_1024%IKE
SPI in: 806122034 out: 3777726982
tnsr-home tnsr#
It will be interesting to see how this goes. The Vyos fork of Vyatta looks like it has had some new life breathed into it, and it appears ATT is sending DANOS aka Vyatta back to open source, so there should be some good comparisons to run soon.
Huh, interesting indeed. I all but forgot about Vyatta after ATT swooped them from Brocade during teh Broadcom Firesale of everything Brocade
(yeah we had just bought around 30 VDX 6740’s at teh time, we were stunned… few hundred thousand $'s to a company that was no more… Gulp… Extreme though bought VDX line and that has been OK, they are decent enough to work with… We are refreshing into cisco now)
Hopefully ATT didnt Catbert it (Vyos) up too much. If you get something running, IPSEC race. You already even know my Qualifying time  LOL
LOL
I would be interesting in hearing what your thoughts are on extreme from a customer standpoint. They have recently expressed interest in having us provide support for their equipment in the field.
I just ran into this today.
I’ve been using Vyos for awhile now in my home test lab and I’ve noticed that it also out preforms Pfsense at almost twice the speed on the same spec device. I ran the basic setup on both software applications and just ran iperf from inside to outside (no ipsec yet). If I remember correctly the Vyos send and receive was around 937 Mbits and Pfsense was like 460 Mbits. Vyos is great so far! My main purpose was to test OSPF routing and I was able to set that up with hardly any problems. I set up a mesh with eight routers with one configured as an edge router. Since then I started researching all of the NAT and Firewall options. I now have SNAT and DNAT configurations set to allow all traffic out but block new traffic from outside coming in and port forwarding using multiple IP address on the WAN interface other than the main dedicated IP address. I also have one internal host SNATing to a dedicated external IP address. Thinking about setting up Policy Based Routing soon. I also plan to see if I can get some sort of VPN connection working next. I highly recommend Vyos for any sort of lab or testing and I have plenty of notes and commands if anyone would like to check out what I’ve done so far… And like TNSR, it’s free as well… (At least the latest rolling updates are and a older version)
Extreme from the trenches. Well, all we run are the VDX 6740’s which came over from Brocade.
I cant really speak to in teh field relationship as these switches just dont die.
The one (yes ONE) that did die, the RMA procedure was quick and easy.