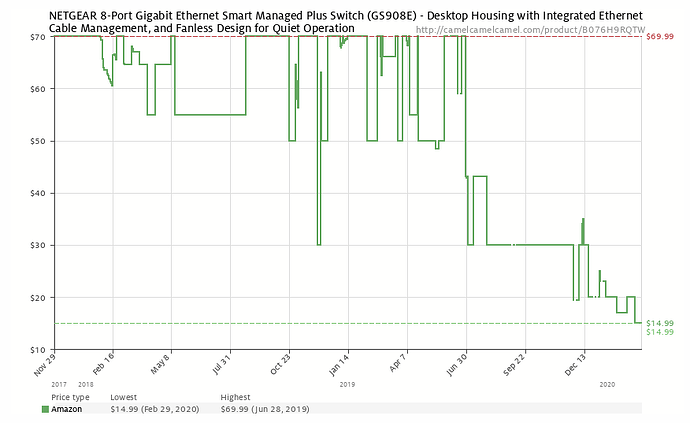
I found out about this from ChessMck on the Ubiquiti forums. Amazon currently has the NetGear GS908E vlan-aware 8 port (plastic case…) switch for $19.99 ASIN B076H9RQTW Tom, you should put an affiliate link to it.
I bought 2 and 2 TP-Link SG108Ev4 and am replacing all the dumb switches at home with vlan-aware switches.
Compared to the TP-Link SG108E v4
TP-Link SG108E advantages: a bit more flexible mirror port (but still rudimentary compared to MikroTik CSS106-5G-1S) If you want port isolation with a single uplink port, the SG108E has what it calls MTU vlan (Multi-Tenant Unit vlans), GS908E does not. Metal case, and smaller size. Easy to get to RJ45 ports.
NETGEAR GS908E advantages: You can name ports, which is useful when configuring vlans and for documentation. More “wife friendly” look (in case you want to put a switch in your bedroom on the nightstand). Has two USB charging (power only) ports. Power supply is beefy 12V 2.5A to support up to 20W for charging devices, but there were some complaints about it getting pretty warm, I assume when charging devices). You can turn the LEDs off, for example if in a bedroom. You can limit access to a specific IP address (but that really isn’t a security feature, more of a deterrent, since it is trivial to change a PC’s IP address.)
Neither of these inexpensive switches is good for a business where you don’t want exposed ports to have access to the management plane, but for learning about vlans, or in a home environment, I don’t see any big disadvantage over dumb switches (but do change the passwords). And neither supports CLI, and no secure communications (only http).
Neither support SNMP or allow you to view the MAC address table, which is a really useful feature when you don’t know which port and cable goes to another device you know the mac address of (from a bundle of cables, all looking the same), so tagging the cables with labels is still a good thing to do.
Both handle vlans, and the setup is similar and not well thought out in my opinion.
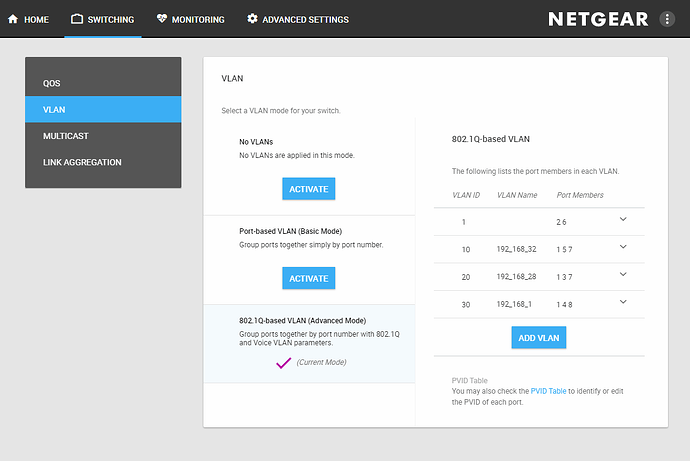
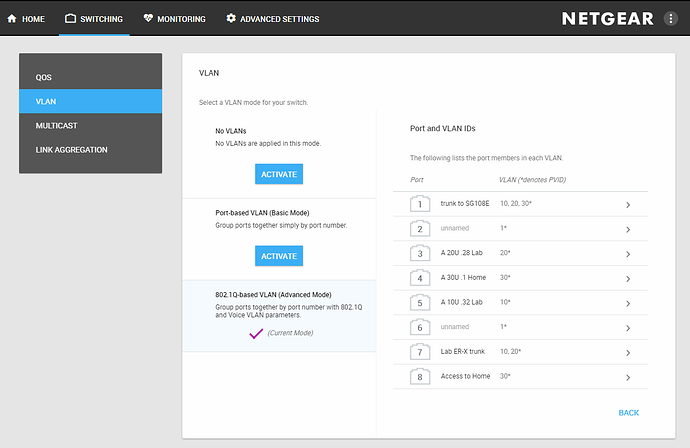
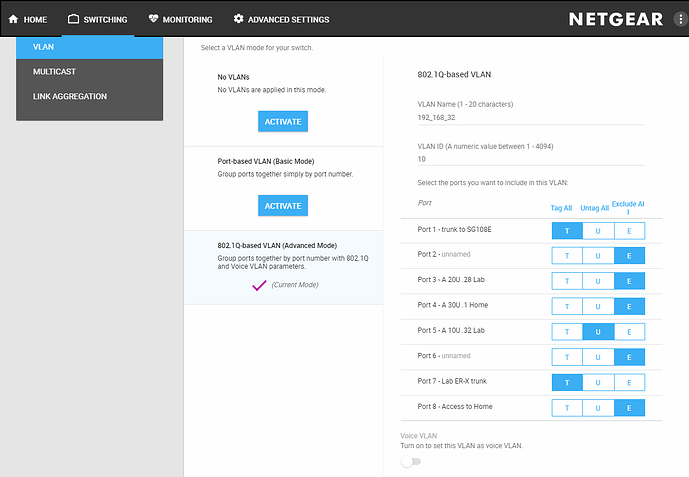
See Tom’s youtube video for SG108E vlan setup, here are some screenshots of the vlan-setup on the GS908E
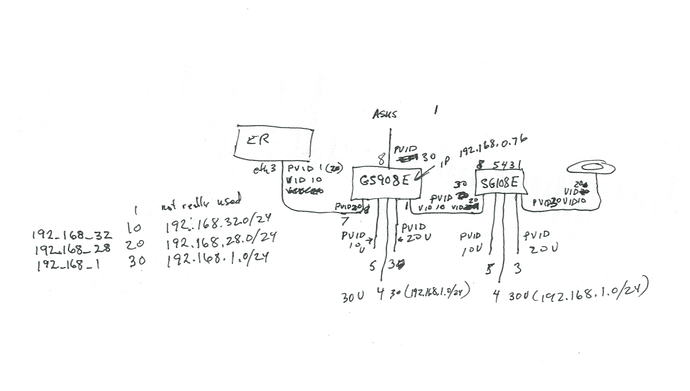
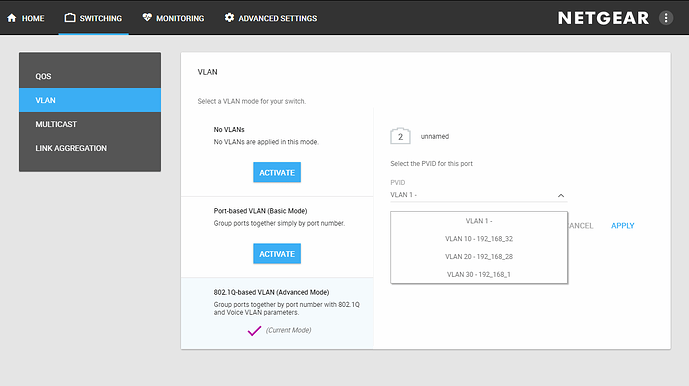
First my chicken scratch diagram I used to setup the lab. Then the screen shots.
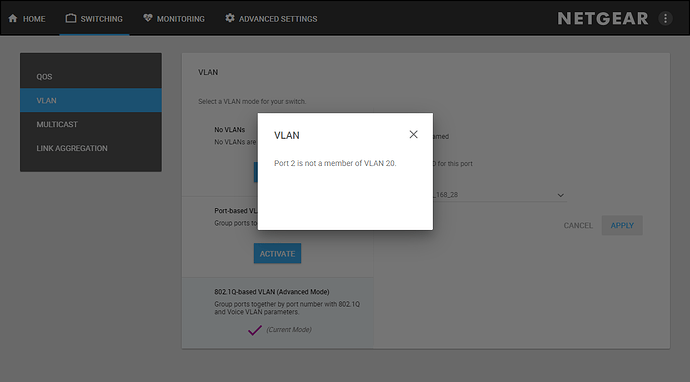
The above is an example of poor design, it shows vlans that the port is not a member of, but it offers all defined vlans.
but then gives an error if you choose one that the port is not a member of.
For $20 it gets my “buy for home or learning” recommendation (especially if you are on a budget).
Edit: 2020-02-01 Per @ChessMcK’s suggestion, Here is a photo with some of my lab network devices.
Back left to right: EdgeRouter X SFP with box and power supply, MikroTik RB260GS/CSS106-5G-1S with box and power supply, 11.5 oz (340 ml) beverage can for size reference, TP-Link SG108E with box and power supply, Netgear GS908E with box and power supply
Front left to right: EdgeRouter X box and power supply, Raspberry Pi 4B 4GB with box, 12 inch stainless steel ruler for size reference.