I want to setup vpn access for remote users and I want to use 2FA login.
I started following Tom’s tutorial freom 2020:
First off – is this [almost] five year old tutorial still a good starting point?
Second off – which path is better:
Path 1 = follow Tom’s tutorial then add FreeRadius w/ user name + pin code and one time password (via some authenticator app such as “google authenticator”)
Path 2 = follow some new/alt tutorial (I am unaware of so far) geared to start-to-finish everything in one guide
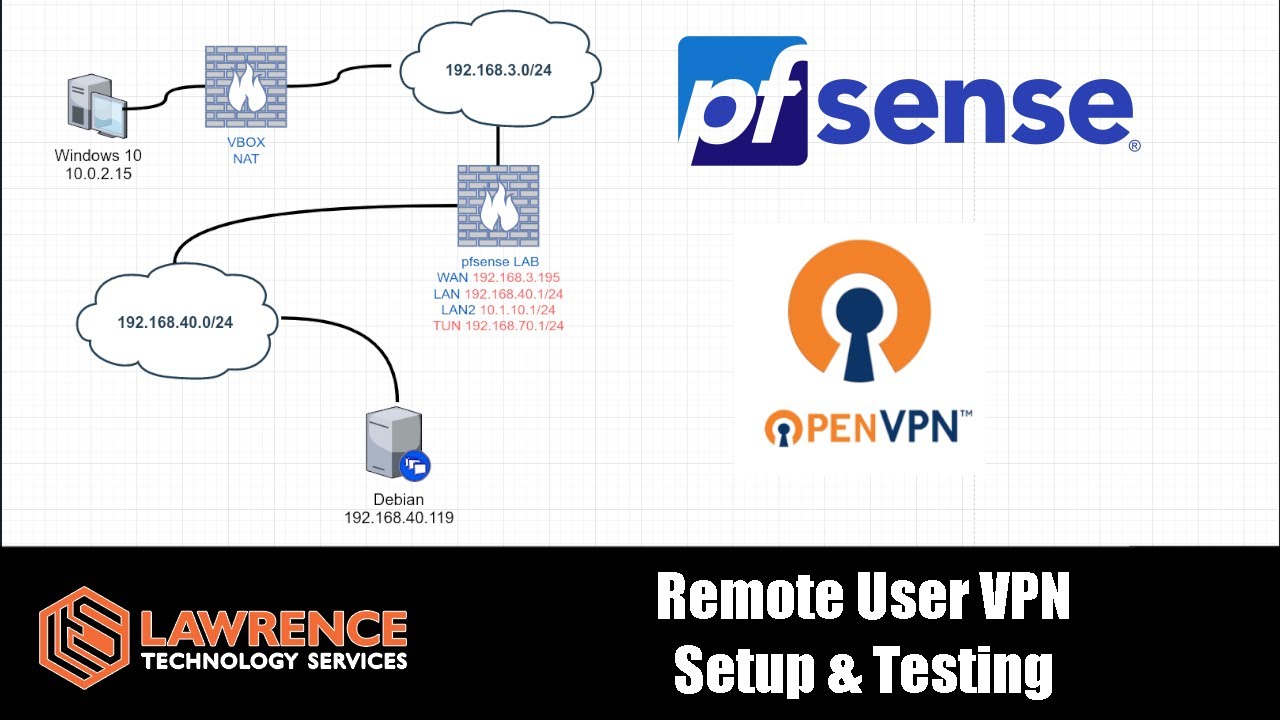
Here is some background info on the situation:
– Everything is self-hosted on premise.
– Everything will be a virtual machine.
– Since I am on a hobby budget, and only used by myself, I would prefer to use self-signed certificates
My Two (2) Use Case Goals:
– Goal #1 = I will primarially be using this to remote in from my Windows 10/11 tablet
– Goal #2 = probably a separate vpn profile from vpn profile for windows users?
I would like to be able to use this to remote in from my two iOS devices running iOS v17/18 (iPhone XS) and iOS 15 (iPhone 6s without SIM)
My One (1) Odd Ball “bonus-if-possible” Use Case Scenario:
– Bonus = probably a separate vpn profile from vpn profile for windows users and iOS users?
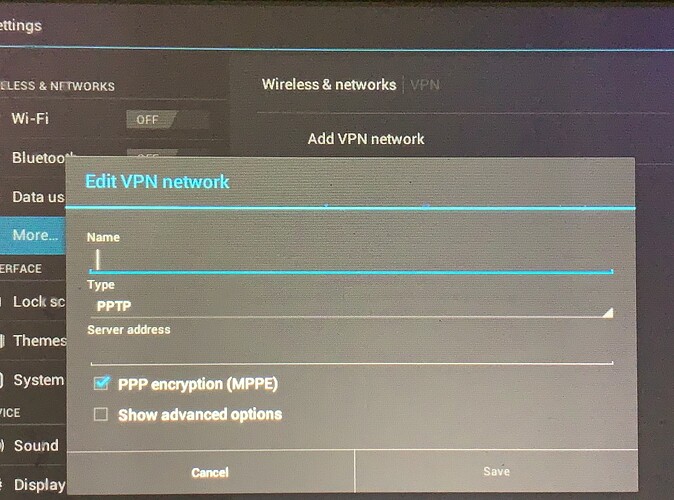
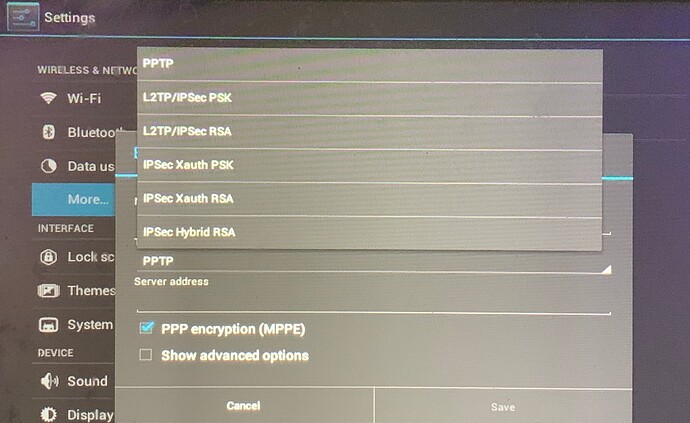
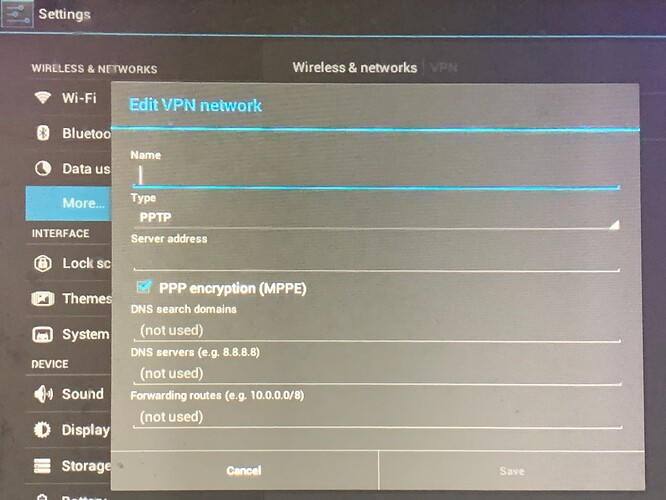
[see attached photos of config options in UI]
I have an old ‘fire sale’ $99 HP TouchPad tablet. I use it for my e-reader.
It would be super extra aweseome swell if I could use this to remote in from my HP Touchpad running Cyanogenmod “9.0.0-RC0-Touchpad-alpha0.6”
yes that is Android Ice Cream Sandwitch v4.0.3
it is de-googled, no google services
Android 4.0.3’s native VPN options are:
Type = PPTP, LTTP/IPSec: RSA, IPSex: Xauth PSK, IPSec: Xauth RSA, and IPSec: Hybrid RSA
Server Address = my IP
Enable PPP encryption (MPPE)
DNS Search domains
DNS Servers (this would presumably be my internal Windows Domain Controller Server)
Forwarding Routes