Good morning all,
Full disclosure i’m posting this in a few forums to gather information, and so if you are a member of many forums you may see this thread pop up in duplicate.
I need help, not really afraid to say that … i need to provide a good solid solution and want to do due diligence and full research to dig in to pros and cons.
So straight into the Background
- Small to medium business center
- Multiple tenants
- Multiple tenant spaces
The services are currently:
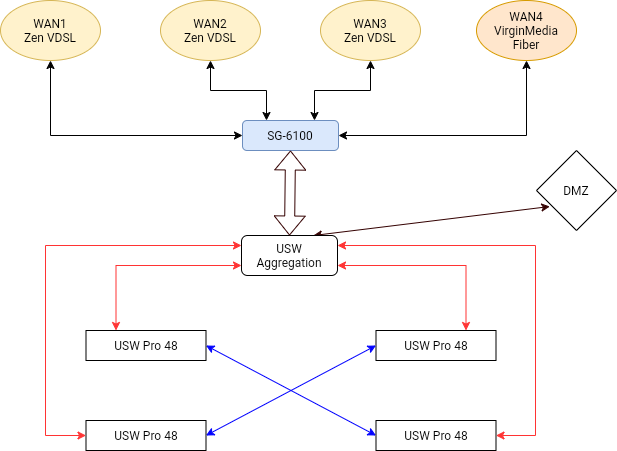
- 3x VDSL lines each with 5 static IPs
- 1x fiber line with 5 static IPs
Peplink Balance 380 balance/router/VPN feeds out a single LAN connection to 6x generic netgear switches, configured with VLANS from the Peplink in segments.
No warranty on all devices, experiencing serious slowness as the peplink only has the ability to do 140mbps throughput. Constant drop out of lines due to high CPU load. Switches are making some serious rattling noises, and no one has the password to them only the config layout in a spreadsheet of whats setup on the ports VLAN wise.
Current use case:
The building provides internet in the form of a VLAN for each tenant space with an associated DHCP scope. Some tenants use the wall sockets in their spaces to access the internet, some tenants install their own routers to a single outlet and configure their own networks. This is inherited over many years and is just the way it is.
A few tenants pay for a static IP address and attach VoIP to this as well as other options. The business center does not allow the installation of tenants own internet lines.
Proposed
Replace all infrastructure due to warranty, age and lack of access. WiFi is not currently in scope as this is not provided currently to any tenant, this is another reason tenants use their own off the shelf garbage routers in the building.
Replacing with a full unifi stack of switches, most likely an aggregation and 4x48 port variety.
My question is the head end. The top of the stack. What should i go with?
UDM Pro? i realize is not the worlds best, however it is what i know. It obviously doesn’t do multi WAN connection, just a single WAN and Fail-over. And so this would be the first change that all tenant’s would have to change their Static IPs to the main line in.
pfSense?, Would i be able to keep the current balancing etc with a pfSense box like a 6100?
Another solution?
Would keeping the Peplink balance purely for link balancing and aggregation, then feeding to a UDMP work? The UDMP allows multiple WAN addresses now and so this could potentially work? And all the VLAN could be done there.
Or another solution totally …
Please be constructive with comments etc, i’m only in the planning stages however the project will most definitely go ahead in one way or another. I would rather not push the business center and all tenants to completely change the way that they work. This i believe would not happen.