Will try to keep this explanation as simple as I can.
I work with a lot of radio gear that used IP networking to communicate between devices. Usually, these devices are segregated onto their own network, untouched by a Firewall or Router. When a device needs to connect for management, like a Windows PC, it is usually only on that isolated network, or has dual NICs. In bigger installations, routers can be used to allow communication from other networks on certain ports. Typical stuff. More info on the gear itself found at https://www.wheatstone.com/, though the gear itself does not so much matter for this situation.
Some of these devices can run their own custom programs. These programs must be uploaded into the devices. These are typically written and compiled on a Windows PC, and the binaries sent via a GUI program that runs on Windows.
As part of my business, I write these programs. And in today’s world, I am doing this more remotely. While it’s easy to remote into a PC, paste my code into the GUI, and upload to a device…it makes debugging complicated. As most of these programs react to button presses, fader movements, etc…
The program I am now writing is for a radio station in Oregon. I am in South Carolina. The company that has sold the program has a test lab in Minnesota. The radio station in Oregon has shipped the device to me that the program will live on. It is a little radio mixer.
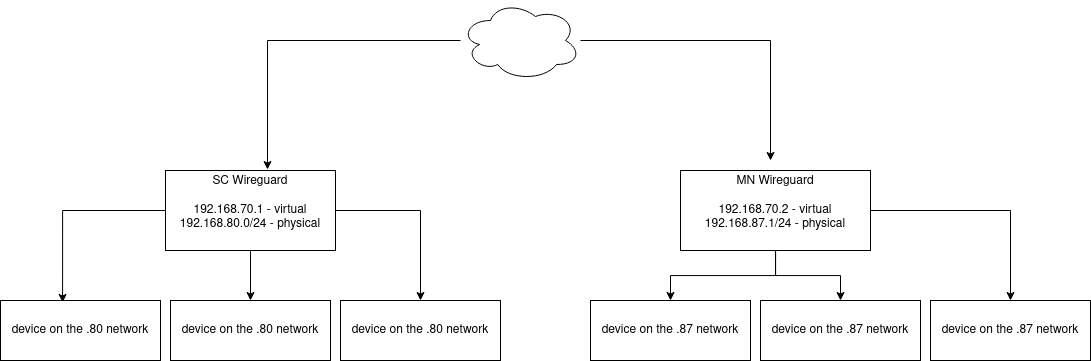
I need to make the mixer communicate from my house in SC to the test lab in Minnesota. So, basically, I need to extend a 192.168.87.x network in Minnesota into my home office. I have pfSense and a Ubiquit Unifi switch in my office. The test lab has a consumer router / firewall. In the Minnesota test lab, there is a standard network for internet, and simply a switch (probably unmanaged) for the WheatNet network (the 192.168.87.x/24 network). There is one Windows PC I can get into and it has two NICs…one for each of these networks.
I have looked into using ZeroTier to bridge back to my home office, but I don’t believe this will work as bridging only seems to be supported on the same interface that provides Internet access to ZeroTier, as far as I can tell. I imagine Nebula is the same, though I have not investigated it fully.
I think my best option is to ship a pfSense to the Minnesota test lab and have someone connect it to both networks, then use OpenVPN to get the WheatNet network into my home office via my pfSense here.
Does anyone have any thoughts of how I could accomplish this in some other way? Any pitfalls with going the OpenVPN / pfSense route?
Chris