I use pfSense with a few Ubiquiti switches/APs for a small home network. I divided the network into several VLANs for the usual Servers, IOT, Security Cameras, etc.
My Ubiquiti devices are connected to the LAN interface, and I also derive the several VLANs from this interface.
For the Unifi APs (U6-lite), I set the “Management VLAN” to default, and I have a port profile that passes three VLANs to the AP which then appear as three SSIDs.
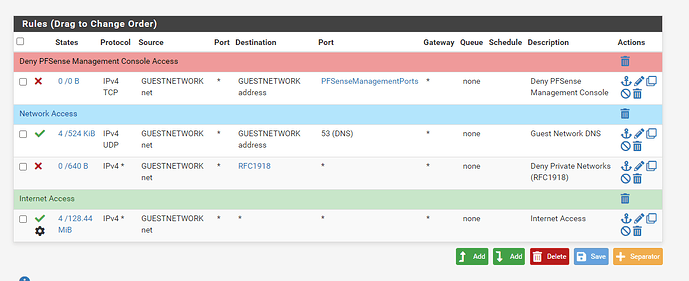
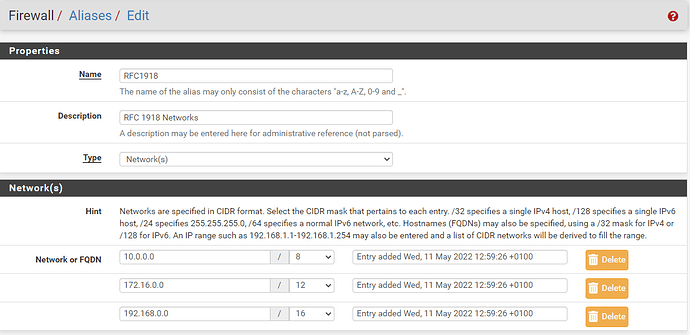
I seem to be getting leakage from other VLANs onto the LAN network. I think this because I see Snort alerts on LAN that show source and destination addresses that are not from that LAN. Also, if I run a packet capture on LAN and view it in wireshark, I see this traffic.
The network is generally working – i.e. I can connect fine, etc…
I have seen some discussion online about Ubiquiti APs needing a bit of special treatment (they like to live on the default network). What am I doing wrong? Is there some peculiarity I’m unaware of? I am pretty familiar with networking back in the days of bridges and routers and thinwire, etc. But, VLANs are newish. In the past, I’ve viewed them as synonymous with “subnet”, but I’m not sure that’s quite true.
Any suggestions?
Thanks,
Marty Wise
Gloucester, Virginia, USA