Well the problem is that I don’t want to open the PFSense WebUI to the WAN. So, it would be nice if I could, but from what I know about using Certbot on my HomeLab, it requires access on port 80.
That isn’t how that works. You can use API’s like cloudflare or whatever DNS provider you use to get a certificate. No open ports necessary.
Oh nice. I do use Cloudflare. Can I use my local area network URL, home.arpa? (The full URI is https://tanwenfirewall.home.arpa).
That you cannot do. You need a public domain that you own for LE to work. If you plan on not doing that then you would generate your own self signed CA and generate certificates from there. You’ll have to install your CA on all your devices though to trust it.
Well, I own several domains that I can use. However, those domains have public access. I like keeping my Firewall WebUI inaccessible from the WAN. I use Wireguard for remote management if I need that.
Again, if you are using the API it won’t need access to your WAN interface. It is all done through your DNS provider.
K, it seems to work, but routing doesn’t work. Do I need to add an entry in my /etc/hosts file? I do have hairpen NAT enabled.
You have to have proper DNS records for your local services, otherwise you will run into DNS rebind attack.
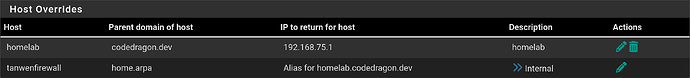
I added these to the DNS resolver settings in PFSense:
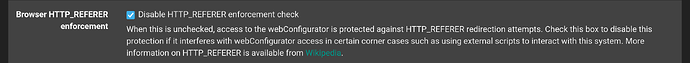
But I also had to do this in System > Advanced > Admin Access:
Not sure that that’s the right way to do things.
@LTS_Tom has an excellent video on HAProxy and Let’s Encrypt certificates: https://youtu.be/bU85dgHSb2E Give it a watch; I’m sure it can point you in the right direction.
While HAProx is great, I don’t put that for the only access pfsense web UI because if something goes wrong in HAProxy you will be locked out.
I’ve tried following it, even before @trentc suggested that video, honestly. But I am doing something wrong. I don’t have a TrueNAS system, so I am using my OpenWRT WAP as the guinea pig, and I keep getting served the self-signed cert when I try to access it from the URI I’m using: https://openwrt.homelab.codedragon.dev
Is there a distinction between a layer three switch and a layer 2 smart switch?
Layer 3 is routing. Layer 2 is for networking (like VLANS). The “smart” portion is describing VLAN functionality.
K. So if not for only VLANs, why would you go for a layer 3 switch over a layer 2 “smart” switch.
To do routing on the switch instead of using a firewall/router. You can still create VLAN’s on a layer 3 switch.
So I just went to Ubiquiti’s store to get a couple of their flex mini switches because they appear to support VLANs and they’re dirt cheap, and I noticed that they just released a new U7 AP lite. I’ve been wanting WiFi 7 to replace my U6 Lite, but I haven’t gotten one because they’re all so expensive, but with this I feel like I just hit the jackpot. Not sure what I’ll do with my U6 Lite. Maybe turn it into a guest network ![]()
So I tried to flash Ubiquiti’s firmware back to my U6 Lite and I bricked it. I can’t even recover it from TFTP Recovery mode. Oh well. It’s been replaced by the U7 lite anyway. Though, I’m kinda disappointed that the U7 doesn’t have a 6Ghz band. Can it even be considered WiFi 7 at that point? Regardless, I ran a speedtest from my laptop and surprisingly got a score double what I used to get with the U6 lite running OpenWRT. A few times I considered maybe comparing UniFi software with OpenWRT on the same hardware, but at the time it was my only AP, so I avoided doing that.
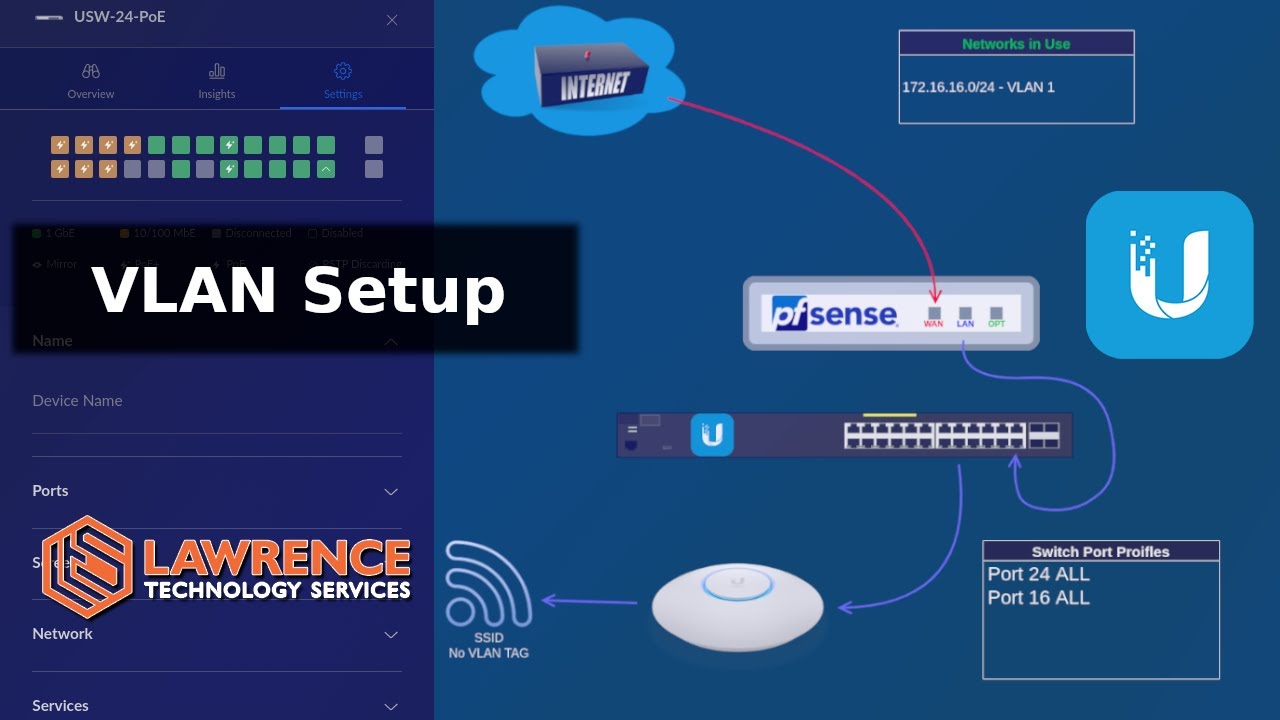
Anyway, with the new switches and UniFi AP, I’m starting to set up the VLANs.
Using Tom’s video here:
I’m just past the part where Tom is going over the VLAN basics, and I have a concern as I start this project. I have a direct connection from my PFSense box to the two UniFi switches, but I wanted a few VLANs ports to output to non-VLAN aware switches. I hope I won’t run into any trouble with that setup.
I know it’s been a little while, but what’s the use-case for this? Why choose a switch over router/firewall?